Цикл інтегрованих уроків з англійської мови тема "Масс медіа" та курсу "Медіа грамотності" 9 клас Урок 4
Урок 4 із цикла інтегрованих уроків з англійської мови та курсу "Медіа грамотності" дозволить учням не тільки освоїти тему "Масс медіа", але й отримати базова знання з медіа грамотності.
- mass media 4.docx docx
- mass media 4.pptx pptx
- scimming ang scanning.mp4 mp4
План-конспект інтегрованого уроку з англійської мови та курсу «Медіа грамотності» з використанням ІКТ у 9 класі №4
Тема: «Мас-медіа»
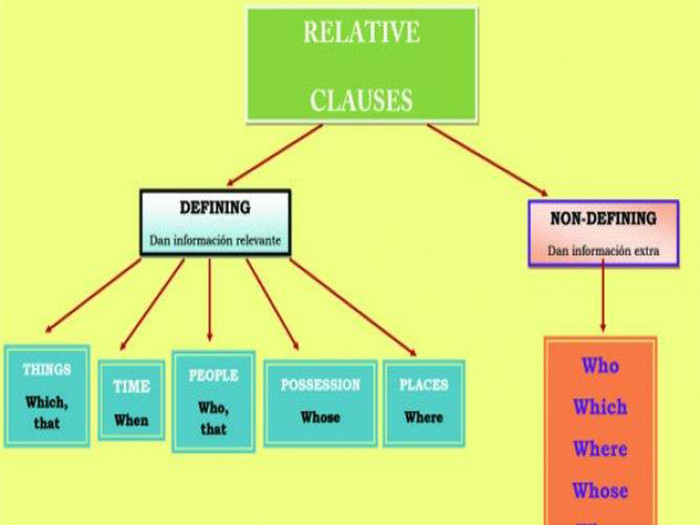
Підтема «Умовні речення. Skimming and scanning.»
Мета уроку (як намір учителя)
Сприяти розвитку в учнів уміння ввічливо висловлювати власні переконання, думки, згоду й незгоду, демонструє основи медіа грамотності, визначає достовірність інформації використовуючи для цього вивчений лексико-граматичний інвентар відповідно до чинної програми та інтегрованої змістової лінії «Громадянська відповідальність».
Очікувані результати (як досягнення учнів)
На кінець уроку учні вмітимуть ввічливо висловлювати власні переконання, що до теми уроку, закріплять лексико-граматичний матеріал, ознайомляться з умовними реченнями, навчаться швидко виділяти головну ідею та знаходити потрібну інформацію у медіа повідомленнях.
Хід уроку:
- Привітання. Організаційний момент.
Hello, pupils. I’m very glad to see you all. How are you? Today we’ll have an unusual lesson.
- Фонетична зарядка (налаштування учнів на сприйняття іншомовного матеріалу).
https://www.youtube.com/watch?v=Mj-dg2Inp4M
- Повідомлення теми та мети уроку. Мотивація учнів.
Today we continue our theme “mass media” and we find out what defining relative clause is and what skimming and scanning is. (слайд 1)
- Актуалізація вивченого ЛМ. Let’s remember words from previous lesson and do this task. (слайд 2-5)
- Розвиток навичок аудіювання. Ex. 4 p72 – listen and choose true or false.
- Введення нового граматичного матеріалу. (слайд 6-7)
- Відпрацювання ГМ. Ex 2-4 p.74-76
- Now we continue learning media literacy and we’ll watch the video where you know what scanning and skimming is. (слайд 8-11)
- And now let’s use your knowledge on practice. I give an article and firstly you need to find out main idea of it, and then find specific information.
Directions: Answer the following questions based on the article below.
Password breach could have ripple effects well beyond Yahoo

![]()
LONDON — As investors and investigators weigh the damage of Yahoo's massive breach to the internet icon, information security experts worry that the record-breaking haul of password data could be used to open locks up and down the web.
While it's unknown to what extent the stolen data has been or will be circulating, giant breaches can send ripples of insecurity across the internet.
"Data breaches on the scale of Yahoo are the security equivalent of ecological disasters," said Matt Blaze, a security researcher who directs the Distributed Systems Lab at the University of Pennsylvania, in a message posted to Twitter.
A big worry is a cybercriminal technique known as "credential stuffing," which works by throwing leaked username and password combinations at a series of websites in an effort to break in, a bit like a thief finding a ring of keys in an apartment lobby and trying them, one after the other, in every door in the building. Software makes the trial-and-error process practically instantaneous.
Credential stuffing typically succeeds between 0.1 percent and 2 percent of the time, according to Shuman Ghosemajumder, the chief technology officer of Mountain View, California-based Shape Security. That means cybercriminals wielding 500 million passwords could conceivably hijack tens of thousands of other accounts.
"It becomes a numbers game for them," Ghosemajumder said in a telephone interview. So will the big Yahoo breach mean an explosion of smaller breaches elsewhere, like the aftershocks that follow a big quake? Ghosemajumder doesn't think so. He said he didn't see a surge in new breaches so much as a steady increase in attempts as cybercriminals replenish their stock of freshly hacked passwords. It's conceivable as well that Yahoo passwords have already been used to hack other services; the company said the theft occurred in late 2014, meaning that the data has been compromised for as long as two years.
"It is like an ecological disaster," Ghosemajumder said in a telephone interview. "But pick the right disaster. It's more like global warming than it is an earthquake. ... It builds up gradually."
The first hint that something was wrong at Yahoo came when Motherboard journalist Joseph Cox started receiving supposed samples of credentials hacked from the company in early July. Several weeks later, a cybercriminal using the handle "Peace" came forward with 5,000 samples — and the startling claim to be selling 200 million more.
On Aug. 1 Cox published a story on the sale, but the journalist said he never established with any certainty where Peace's credentials came from. He noted that Yahoo said most of its passwords were secured with one encryption protocol, while Peace's sample used a second. Either Peace drew his sample from a minority of Yahoo data or he was dealing with a different set of data altogether.
"With the information available at the moment, it's more likely to be the latter," Cox said in an email Tuesday. The Associated Press has been unable to locate Peace. The darknet market where the seller has been active in the past has been inaccessible for days, purportedly due to cyberattacks.
At the moment it's not known who holds the passwords or whether a state-sponsored actor, which Yahoo has blamed for the breach, would ever have an interest in passing its data to people like Peace.
Meanwhile Yahoo users who recycle their passwords across different sites may be at risk. And while an internet-wide password reset is one option, Yahoo's announcement that some security questions were compromised too means that the risks associated with the breach are likely to linger.
A password can be changed, after all, but how do you reset your mother's maiden name?
_____________
Satter, Raphael. (2016, September 27). Password breach could have ripple effects well beyond Yahoo. Retrieved from https://www.yahoo.com/tech/password-breach-could-ripple-effects-100929929.html
1. Skim the article for the main idea. Which of the following best matches the article’s main idea?
1) Passwords stolen from Yahoo might cause a big effect on the rest of the Internet.
2) Online theft is increasing.
3) People should change their passwords.
4) There are many ways to steal online information.
2. Вопрос 2 Scan for numbers: When were the passwords stolen from Yahoo?
- 2013
- 2014
- 2015
- 2016
Вопрос 3 Scan for numbers: How many passwords was the thief selling?
- 5,000
- 10,000
- 200 million
- 500 million
Вопрос 4 Scan for information: What is Joseph Cox's job?
- Security researcher
- Cybercriminal
- Chief technology officer at Mountain View
- Journalist
- Рефлексія. «Куб Блума»
- Домашнє завдання. Prepare an article and questions for it.
Використані джерела:
- https://www.coursera.org курс «English for Media Literacy» від автор: Пенсильванский университет


про публікацію авторської розробки
Додати розробку