COMPUTER BASICS OVERVIEW
Part II
COMPUTER BASICS OVERVIEW
Text A
Reading.
- Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
A COMPUTER
The word “computer” has been part of the English language since 1646, but if you look in a dictionary printed before 1940, you might be surprised to find a computer defined as a person who performs calculations! Prior to 1940, machines designed to perform calculations were referred to as calculators and tabulators, not computers. The modern definition and useage of the term “computer” emerged in the 1940s, when the first electronic computing devices were developed.
Most people can formulate a mental picture of a computer, but computers do so many things and come in such a variety of shapes and sizes that it might seem difficult to distill their common characteristics into an all-purpose definition. At its core, a computer is a device that accepts input, processes data, stores data and produces output, all according to a series of stored instructions.
Computer input is whatever is typed, submitted, or transmitted to a computer system. Input can be supplied by a person, the environment, or another computer. Examples of the kinds of input that a computer can accept include words and symbols in a document, numbers for a calculation, pictures, temperatures from a thermostat, audio signals from a microphone, and instructions from a computer program. An input device, such as a keyboard or mouse, gathers input and transforms it into a series of electronic signals for the computer to store and manipulate.
In the context of computing data refers to the symbols that represent facts, objects, and ideas. Computers manipulate data in many ways, and this manipulation is called processing. The series of instructions that tell a computer how to carry out processing tasks is referred to as a computer program, or simply a “program”. These programs form the software that sets up a computer to do a specific task. Some of the ways that a computer can process data include performing calculations, sorting lists of words or numbers, modifying documents and pictures, keeping track of your score in a fact-action game, and drawing graphs. In a computer, most processing takes place in a component called the central processing unit (CPU), which is sometimes described as the computer’s “brain”.
A computer stores data so that it will be available for processing. Most computers have more than one place to put data, depending on how the data is being used. Memory is an area of a computer that temporarily holds data waiting to be processed, stored, or output. Storage is the area where data can be left on a permanent basis when it is not immediately needed for processing. Output is the result produced by a computer. Some examples of computer output include reports, documents, music, graphs, and pictures. An output device displays, prints or transmits the results of processing.
Take a moment to think about the way you use a simple handheld calculator to balance your checkbook each month. You’re forced to do the calculations in stages. Although you can store data from one stage and use it in the next stage, you cannot store the sequence of formulas – the program – required to balance your checkbook. Every month, therefore, you have to perform a similar set of calculations. The process would be much simpler if your calculator remembered the sequence of calculations and just asked you for this month’s checkbook entries.
Early “computers” were really no more than calculating devices, designed to carry out a specific mathematical task. To use one of these devices for a different task, it was necessary to rewire its circuits. In a modern computer, the idea of a stored program means that a series of instructions for a computing task can be loaded into a computer’s memory. These instructions can easily be replaced by a different set of instructions when it is time for the computer to perform another task.
The stored program concept allows you to use your computer for one task, such as word processing, and then easily switch to a different type of computing task, such as editing a photo or sending an e-mail message. It is the single most important characteristic that distinguishes a computer from other simpler and less versatile devices, such as calculators and pocket-sized electronic dictionaries.
Comprehension check.
- Mark the following statements as True or False.
1. A computer can be defined by its ability to perform different mathematical and logical operations according to a set of instructions.
2. Computers had already been used before WWII.
3. There is no any significant difference between memory and storage.
4. Computer programs and software mean the same.
5. CPU is a part of a computer that controls all other parts of the system.
6. Computers and calculators are very similar devices which are based on the stored program concept.
Vocabulary practice.
- Match the words with their synonyms.
supply unit
distinguish appear
purpose but
device open
emerge goal
available differentiate
although provide
- Which word does not belong to the group?
a) input carry out output process
b) hold store keep perform
c) edit data transmit set up
d) software storage supply memory
e) accept refer input load
f) unit device software equipment
- Complete the following sentences choosing one out of the variants given.
1. If you don’t back up regularly, you can lose all your … .
a) CPU b) programs c) data d) storage
2. A computer … input, processes and stores data, produces output according to a series of instructions.
a) accepts b) submits c) emerges d) transmits
3. Reports, documents, graphs and pictures can be … to as computer output.
a) performed b) supplied c) transformed d) referred
4. A computer can perform various tasks such as word processing or sending messages that … it from any calculator.
a) set up b) distinguish c) keep track d) mean
5. Memory is the part of a computer where data and instruction are stored … .
a) permanently b) available c) temporarily d) versatile
6. Data is processed in the … according to the instructions that have been loaded into the computer memory.
a) CPU b) variety c) storage d) output
- Make two-word expressions connected with computing by combining words from two lists: A and B. Then match each expression with the appropriate phrase.
A: stored B: processing
permanent device
word output
handheld storage
input calculator
computer program
1. A small electronic instrument allowing you to do mathematical functions.
2. A set of instructions understood by a computer and kept in its memory.
3. A piece of equipment, such as a mouse or keyboard.
4. A form of volume in which information can be stored for a long time.
5. The use of a computer to edit, format, store or print a piece of text.
6. Reports, music, documents and pictures produced by a computer.
- Restore the instructions for switching a computer by matching the beginnings with the endings and put them into the correct order.
Beginnings Endings
1. if a message asks a) for your computer and turn it on.
2. locate the power switch b) desktop to appear.
3. then press the Enter key c) for your user ID or password,
type them in.
4. wait for the Windows d) connected to your computer and turn them on.
5. locate the power switch e) on your computer’s keyboard.
for any devices
- Fill in the gaps.
A computer is a ___ that accepts input, ___ data, stores data, and produces out put according to a series of stored instructions. Before a computer processes data, it is temporarily held in ___. This data is processed in the ___. The idea of ___ program means that a series of instructions for a computing task can be loaded into a computer’s memory.
Speaking.
- Discuss the following questions.
- How old is the word “computer”?
- What is a computer?
- What can be called “computer input”?
- What input devices can you name?
- Why do we need software?
- What is the purpose of the CPU?
- How do memory and storage differ?
- What computer output can we get?
- What’s so significant about a computer’s ability to store instructions?
- What does a stored program mean?
Text B
Pre-reading.
- Match the terms with the appropriate definitions.
|
a desktop computer |
a) this computer is especially suited for storing and distributing data on a network; these machines do not include features such as sound cards, DVD players, and other fun accessories; they don’t require specific hardware and just about any computer can be configured to perform such work; |
|
a notebook |
b) these are powerful desktop computers designed for specialized tasks; they can tackle tasks that require a lot of processing speed, most have circuitry specially designed for creating and displaying three-dimensional and animated graphics and often dedicated to design tasks; |
|
a tablet computer |
c) it’s a large and expensive computer capable of simultaneously processing data for hundreds or thousands of users; used by businesses or governments to provide centralized storage, processing and management for large amount of data in situations where reliability, data security and centralized control are necessary; |
|
a handheld computer |
d) it fits on a desk and runs on power from an electrical wall outlet; its keyboard is typically a separate component, connected to the main unit by a cable; |
|
a workstation |
e) it’s a portable computing device featuring a touch-sensitive screen that can be used as a writing or drawing pad; |
|
a mainframe computer |
f) it’s one of the fastest computers in the world; can tackle complex tasks such as breaking codes, modeling worldwide weather systems and simulating nuclear explosions; |
|
a supercomputer |
g) it features a small keyboard or touch-sensitive screen and is designed to fit into a pocket, run on batteries and be used while you are holding it; also called a PDA (personal digital assistant), it can be used as an electronic appointment book, address book, calculator and notepad; |
|
a server |
h) it’s a small lightweight personal computer that incorporates screen, keyboard, storage and processing components into a single portable unit, also referred to as a “laptop”. |
Reading.
- Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
PERSONAL COMPUTER SYSTEMS
The term “computer system” usually refers to a computer and all the input, output, and storage devices that are connected to it. A personal computer system usually includes the following equipment:
- system unit.
The system unit is the case that holds the main circuit boards, microprocessor, power supply, and storage devices. The system unit of the notebook computer holds a built-in keyboard and speakers, too.
- display device.
Most desktop computers use a separate monitor as a display device, whereas notebook computers use a flat panel LCD screen (liquid crystal display screen) attached to the system unit.
- keyboard.
Most computers are equipped with a keyboard as the primary input device.
- mouse.
A mouse is an input device designed to manipulate on-screen graphical objects and controls.
- hard disk drive.
A hard disk drive can store billions of characters of data. It is usually mounted inside the computer’s system unit. A small external light indicates when the drive reading or writing data.
- CD and DVD drives. A CD drive is a storage device that uses laser technology to work with data on computer or audio CDs. A DVD drive can work with data on computer CDs, audio CDs, computer DVDs, or DVD movie disks. Some CD and DVD drives are classified as “read only” devices that cannot be used to write data onto disks. They are typically used to access data from commercial software, music, and movie CDs or DVDs. “Writable” CD and DVD drives, however, can be used to store and access data.
- floppy disk drive.
A floppy disk drive is a storage device that reads and writes data on floppy disks.
- sound card and speakers.
Desktop computers have a rudimentary built-in speaker that’s mostly limited to playing beeps. A small circuit board, called a sound card, is required for high-quality music, narration, and sound effects. A desktop computer’s sound card sends signals to external speakers. A notebook’s sound card sends signals to speakers that are built into the notebook system unit.
- modem and network cards.
Many personal computer systems include a built-in modem that can be used to establish an Internet connection using a standard telephone line. A network card is used to connect a computer to a network or cable Internet connection.
- printer.
A computer printer is an output device that produces computer-generated text or graphical images on paper.
The term peripheral device designates equipment that might be added to a computer system to enhance its functionality. Popular peripheral devices include printers, digital cameras, scanners, joysticks, and graphics tablets.
The word “peripheral” is a relatively old part of computer jargon that dates back to the days of mainframes when the CPU was housed in a giant box and all input, output, and storage devices were housed separately. Technically, a peripheral is any device that is not housed within the CPU.
Although a hard disk drive seems to be an integral part of a computer, by the strictest technical definition, a hard disk drive would be classified as a peripheral device. The same goes for other storage devices and the keyboard, monitor, LCD screen, sound card, speakers, and modem. In the world of personal computers, however, the use of the term “peripheral” varies and is often used to refer to any components that are not housed inside the system unit.
Comprehension check. .
- Indicate the paragraph where the following ideas are found in the text.
1.When the drive is being used a small light indicator is on.
2.Sound characteristics of different computers vary.
3. This device is most suitable for controlling the position of the cursor.
4. It’s a device to use Internet via a phone line.
5. This system is represented by different interlinked input, output and storage
devices.
6. There is a storage device that uses laser technology.
Vocabulary practice.
- In the text find the opposites to the given words and make up a story.
internal rough unfasten secondary reduce successively
- Put the letters in the following words into correct order.
peroayrtilm netmipqeu literesav hpelarepir afuteer beroadyk
- Complete the following sentences choosing one out of the variants given.
1. Which of the following statements about hard disk is not true?
a) it stores data b) it’s not a peripheral
c) it’s a magnetic device d) it’s placed inside a computer
2. This storage format is used to store digital video or computer data.
a) a floppy disk b) CD c) a sound card d) DVD
3. What are the elements of a computer system?
a) disk drives b) a monitor
c) a central processor d) all of the above
4. These portable computers are ideal for mobile users. They are easy to carry and can be used outdoors without the need for an electrical outlet.
a) mainframes b) notebooks c) workstations d) servers
5. Which of the following functions can a floppy disk drive perform?
a) store data b) read data c) write data d) all of the above
6. This electronic device has a special pen and acts like an electronic piece of paper transferring images to the computer screen.
a) a laptop b) PDA c) a tablet computer d) a mainframe
- Make three-word expressions connected with computing combining words from three lists: A, B and C. Then match each expression with the appropriate phrase.
A: central B: circuit C: disk
liquid video network
hard processing drive
main crystal unit
digital area display
local disk board
1. This computer network is located within a limited geographical area such as a small business or a university lab.
2. The part of a computer that controls all the other parts of the system.
3. An electronic device that is used to display information in many calculators and portable computers.
4. A central flat card used as a base on which electronic components are placed and then connected together by wires.
5. A type of volume used for storing movies.
6. A disk drive that passes data to or from the hard disk and the computer.
- Transform the following sentences without any change in meaning. Use the prompts as they are given (words in brackets, parts of sentences).
1. The factory is equipped for computer controlled production.
The factory has … for … .
2. This is our system for storing client records (provides).
3. Only privileged users can access this information.
Only privileged users have … .
4. This device is primarily used to connect different peripherals (establish).
5. This device can perform a huge variety of functions.
The functions … greatly.
6. Almost any equipment that can be attached to a computer to enhance its functionality is called a peripheral (designates).
6. Fill in the gaps in the text.
Computers are grouped into categories, such as ___ computers, handhelds, mainframes, supercomputers, servers, workstations, and videogame ___. A ___computer is a type of microcomputer designed to ___ the needs of an individual while ___ are very expensive and used for very specific and complex ___.
Speaking.
- Discuss the following questions.
- What are the characteristics of desktop computers?
- How do notebook computers differ from desktops?
- What is a tablet computer?
- What is a hand held and what is it used for?
- What type of computers can be classified as workstations?
- What’s so special about a mainframe computer?
- How powerful is a supercomputer?
- What makes a computer a “server”?
- What does a personal computer system include?
- What’s a peripheral device and can a hard disk be called so?
Critical thinking.
- Read the article and express you opinion on the problem.
Digital Rights Management
Suppose you purchase a music CD of your favorite recording group. Now you want to transfer the file to your computer, rip the best tracks, and transfer them to your portable audio player. But wait! That CD is copy protected and your computer CD drive won’t read it. You purchased the disk. Can’t you listen to the music on any device you choose? The answer is “yes” and “no”. Yes, copyright law gives you the right to make copies for your personal use and transfer works into a format that works on your equipment. However, the growing pervasiveness of digital rights management may curtail your ability to exercise these rights.
It is easy to copy digital material. Before the dawn of the digital age, copies produced by analog equipment, such as photocopiers and audio tape dubbing machines, were of considerably poorer quality than the originals. Copies of digital materials, however, are indistinguishable from the originals, and that factor has encouraged an alarming increase in software, music, and movie piracy.
The battle against piracy took shape as a concept called digital rights management (DRM), vigorously supported by Microsoft and backed by a host of industry leaders.
Today, digital rights management encompasses a variety of technologies implemented by copyright holders, such as record companies and software publishers, which restrict the usage of digital material. DRM systems address piracy by using a variety of technologies for manipulating data, media, devices, and transactions.
Software copy protection techniques include reading data written to places on a disk or CD-ROM that the drive cannot normally access, using hardware that must be plugged into the computer when the software is run, requiring a serial number during the installation process, and using Internet product activation that checks the validity of an installation. Most software copy protection schemes have proved to be costly for publishers or inconvenient for consumers.
Many consumers are not aware that they pay a surcharge for every blank audio tape or CD they purchase. Collected revenues from this surcharge go to music publishers to compensate recording artists for the fact that many people duplicate works without authorization.
Most of today’s music download sites encrypt music files and embed codes that limit the number of times they can be copied and the devices on which they can be played. Various formats used by different sites are not compatible with each other and require different players. Music from several different download sites cannot be compiled into a single playlist. It is becoming more common for music CDs to use play-protection technology designed to make the CD unusable in devices, such as computer CD-R drives, that can also be conveniently used for duplicating CDs. Consumers who purchase these protected CDs find that they cannot be copied to a computer hard disk, then ripped to produce an MP3 file for a portable audio player.
Commercial movie DVDs use CSS (Content-Scrambling System) encryption to make DVDs playable only on authorized DVD players equipped with decryption key circuitry. Movies purchases in the United States and Canada cannot be played on devices manufactured for the European or Asian markets.
Despite DRM technologies and the inconveniences imposed on consumers, digital piracy remains rampant. According to an article about digital rights management posted on Wikipedia, “To date, all DRM systems have failed to meet the challenge of protecting the rights of the rights holder while also allowing the use of the rights of the purchaser. None have succeeded in preventing criminal copyright infringement by organized, unlicensed, commercial pirates.”
Current DRM technologies do not seem able to distinguish between pirates and legitimate consumers. As a result, DRM technologies essentially pose restrictions on consumers that go beyond the intended limitations of copyright law.
The current status of DRM seems to conflict with the original intent of copyright law to allow consumers to manipulate and copy works for their own use. Can technology eventually offer a solution that prevents piracy, but allows individuals to exercise their rights to fair use of copyrighted materials?
Test 1
- Do the tasks in the following test.
1. The process of transferring a file from a remote computer to your personal computer is called ___.
2. Personal computer systems typically include the following devices EXCEPT ___.
a) a mouse b) a hard disk drive c) a CD-ROM d) a PDA
3. The stored program concept on a computer is the single most important characteristic that distinguishes a computer from other simpler devices such as a calculator. (True/False)
4. Which of the following tasks might you perform with application software?
a) locating data b) starting programs c) both a) and b)
d) creating and editing documents
5. Most computer systems use a(n) ___ as the primary input device.
a) monitor b) keyboard c) mouse d) floppy disk drive
6. Computers can be categorized by type, such as personal computers, handhelds and supercomputers. (True/False)
7. The computer system unit is the case that holds the main circuit boards, microprocessor, power supply and ___ devices.
8. A floppy disk drive is not considered a storage device. (True/False)
9. The __ is often referred to as the “brain” of the computer.
a) keyboard b) monitor c) central processing unit d) software
10. ___ refers to the symbols that represent facts, objects and ideas.
Projects.
- Choose and perform one of the given projects below.
1. Although the Internet provides a global communications network, communication between people still depends on finding a common language. For this project, explore the Web and experiment with ways in which technology is being used to close the language gap. You might start at Google or Wikipedia and look at the selection of languages they offer. Chronicle your exploration, making sure to document the sites you visited. Present your conclusions about Internet use by non-English speakers in writing.
2. Whether you’re taking this course to fulfill a graduation requirement or to improve your career options take a few minutes to evaluate what you expect to gain from this course. Look though the units of this textbook and select the section that you think will be the most useful, interesting and the section that seams to be the least relevant to you. Incorporate your thoughts in two or three paragraphs.
COMPUTER HARDWARE
Text A
Pre-reading. Match the meaning of the following English words with their Russian equivalents.
|
1. digital device |
a) полупроводниковый материал |
|
2. analog device |
b) заголовок файла |
|
3. binary digit |
c) интегральная схема |
|
4. numeric data |
d) цифровое устройство |
|
5. character data |
e) представление данных |
|
6. extended |
f) определять количество |
|
7. digitize |
g) расширенный |
|
8. file header |
h) символ, знак |
|
9. quantify |
i) переводить в цифровую форму, оцифровывать |
|
10. integrated circuit |
j) цифровые данные; числовые данные |
|
11. semiconducting material |
k) двоичная цифра |
|
12. data representation |
l) аналоговое (моделирующее) устройство |
Reading. Read the text and try to guess the meaning of the words in bold face. Check your variants in the dictionary.
DATA REPRESENTATION AND DIGITAL ELECTRONICS
Data representation
People use computers to work with many kinds of data, including numbers, text, music, photos, and videos. Data representation is the process of transforming this diverse data into form (today digital) that computers can use for processing.
Most computers are digital devices which work with discrete – distinct and separate – data, such as the digits 1 and 0. In contrast, an analog device works with continuous data. As an analogy, a traditional light switch has two discrete states – “on” and “off” – so it is a digital device. A dimmer switch, on the other hand, has a rotating dial that controls a continuous range of brightness. It is, therefore, an analog device. Most computers use the simplest type of digital technology – their circuits have only two possible states. For convenience, let’s say that one of those states is “on” and the other state is “off”. When discussing these states, we usually indicate the “on” state with 1 and the “off” state with 0. These 1s and 0s are referred to as binary digits. It is from this term that we get the word “bit” – binary digit. Computers use sequences of bits to digitally represent numbers, letters, punctuation marks, music, picture, and videos.
Numeric data consists of numbers that might be used in arithmetic operations. Computers represent numeric data using the binary number system, also called “base 2”. The binary number system has only two digits: “0” and “1”. No numeral like “2” exists in this system, so the number “two” is represented in binary as “10” (pronounced “ one zero“). In binary you count 0 (”zero”), 1 (“one”), 10 (“one zero”), instead of counting 0, 1, 2 in decimal. The important point to understand is that the binary number system allows computers to represent virtually any number simply by using 0s and 1s, which conveniently translate into electrical “on” and “off” signals.
Character data is composed of letters, symbols, and numerals that are not used in arithmetic operations. A digital computer uses a series of bits to represent letters, characters, and numerals. Computers employ several types of codes to represent character data, including ASCII, EBCDIC, and Unicode. ASCII (pronounced “ASK ee”, American Standard Code for Information Interchange,) requires only seven bits for each character. ASCII requires codes for 128 characters.
A superset of ASCII, called Extended ASCII, uses eight bits to represent each character. Using eight bits instead of seven bits allows Extended ASCII to provide codes for 256 characters. Unicode (pronounced ‘YOU ni code’) uses sixteen bits and provides codes for 65,000 characters.
To work with music and pictures, they must be digitized. The term to digitize means to convert raw, analog data into digital format represented by 0s and 1s. A photograph or drawing can be digitized by treating it as a series of colored dots. Each dot is assigned a binary number according to its color. A digital image is simply a list of color numbers for all the dots it contains. In a similar way, music can be digitized by assigning binary codes to notes.
All the “stuff” that your computer works with is stored in files as a long series of 1s and 0s. Your computer needs to know whether to interpret those 1s and 0s as ASCII code, binary numbers, or the code for a picture or sound. To avoid confusion, most computer files contain a file header with information about the code used to represent the file data. A file header can be read by the computer, but never appears on the screen. By reading the header information, a computer can tell how a file’s contents were coded.
Quantifying Bits and Bytes
Even though the word “bit” is an abbreviation for “binary digit”, it can be further abbreviated, usually as a lowercase “b”. A byte is composed of eight bits and usually abbreviated as an uppercase “B”. Transmission speeds are typically expressed in bits, whereas storage space is typically expressed in bytes.
When working with computers, you’ll frequently encounter references such as “50 kilobits per second”. In common usage, “kilo”, abbreviated as “K”, means a thousand. In the decimal number system we use on a daily basis, the number 1,000 is 10 to the 3rd power, or 10³. In the world of computers where base 2 is the norm, a “kilo” is precisely 1,024, or 2¹º. A kilobit (Kb or Kbit) is 1,024 bits, a megabit is 1,048,576 or 2²º bits, a gigabit is 1,073,741,824 bits or 2³º bits.
Digital Electronics
Because most computers are electronic devices, bits take the form of electrical pulses that can travel over circuits, in much the same way that electricity flows over a wire when you turn on a light switch. All the circuits, chips, and mechanical components that form a computer are designed to work with bits. Most of these essential components are housed within the computer’s system unit. A computer’s system unit typically contains circuit boards, storage devices, and a power supply that converts current from an AC wall outlet into the DC current used by computer circuitry.
The terms “computer chip”, “microchip” and “chip” originated as technical jargon for “integrated circuit”. An integrated circuit (IC) is a super-thin slice of semiconducting material packed with microscopic circuit elements, such as wires, transistors, capacitors, logic gates, and resistors. Semiconducting materials are substances with properties between those of a conductor and an insulator. The assortment of chips inside a computer includes the microprocessor, memory modules, and support circuitry. The computer’s main board, called a system board, “motherboard”, or ”main board”, houses all essential chips and provides connecting circuitry between them.
Comprehension сheck. Mark the following statements as True or False.
1. Both analog and digital devices work with continuous data.
2. The binary system allows computers to represent any number or symbol.
3. The more bits are used for representing a character data – the more is the number of characters provided by a certain code.
4. To know the code used to represent data a computer has to read the file header.
5. The process of digitizing is used to transform digital data into analog ones.
6. The DC is transformed into the AC for the computer to be able to work.
7. An integrated circuit is often referred to as Unicode.
Vocabulary practice
1. Match up the words that are similar in meaning.
|
1. rotate 2. allow 3. employ 4. require 5. provide 6. interpret |
a) permit b) understand c) spin d) ensure e) need f) apply |
2. Fill in the blanks choosing from the variants given.
1. Main memory … only a small amount of storage area for the data and instructions required by the CPU.
a) allows b) transforms c) provides d) rotate
2. To fabricate a chip, the conductive properties of selective parts of the … can be enhanced.
a) electrical pulses b) semiconducting mater c) digital devices d) binary numbers
3. Some chips on the motherboard are plugged into special sockets and connectors that … chips to be removed for repairs.
a) allow b) assign c) avoid d) include
4. Even embedded computers … maintenance by people.
a) transform b) range c) employ d) require
5. The most powerful computer systems with the fastest processing speed … supercomputers.
a) rotate b) are referred to as c) avoid d) include
6. Every key stroke on a keyboard … a letter symbol into a digital code that the machine can understand.
a) converts b) requires c) allows d) provides
7. Most computers … the simplest type of digital technology – their circuits have only two possible states.
a) assign b) employ c) require d) range
3. Make two-word expressions combining words from two lists. Then fill in the gaps in the following sentences. Some words can be used more than once.
A: data B: data
diverse digit
integrated header
binary circuit
file representation
character
numeric
1. The binary number system represents … as a series of 1s and 0s.
2. An … contains microscopic elements such as wires, transistors, and capacitors, that are packed onto a very small square of semiconducting material.
3. The process of transforming data into form that computers can use for processing is referred to as … .
4. Today computers typically represent … digitally.
5. A computer treats the letters and symbols in a word as … which can be represented by a string of 0s and 1s.
6. All the material your computer works with is stored in files as long strings of … .
7. A … is stored along with the file and contains information about the code used to represent the file data.
4. Fill in the gaps in the text.
Most of today’s computers are electronic, digital devices that work with data coded as binary digits, also known as ___. To represent numeric data, a computer can use the ___ number system. To represent character data, a computer uses Extended ___, EBCDIC, or Unicode. These codes also provide digital representations for the numerals 0 through 9 that are distinguished from numbers by the fact that they are not typically used in mathematical operations. Computers also ___sounds, pictures, and videos into 1s and 0s.
A ___ is a single 1 or 0, whereas a ___ is a sequence of eight 1s and 0s. Transmission speeds are usually measured in ___, but storage space is usually measured in ___ or gigabytes.
Speaking. Discuss the following questions.
1. What is data representation?
2. How do computers represent data digitally?
3. How can a computer represent words and letters using bits?
4. How does a computer convert music and pictures into codes?
5. When a computer works with a series of 1s and 0s, how does it know which
code to use?
6. How can you tell the difference between bits and bytes?
7. What do the prefixes kilo-, mega- and giga- mean?
8. How does a computer store and transport all those bits?
9. What’s a computer chip?
10. What provides connectivity between all the constituent parts of the computer?
Text B
Pre-reading.
- Match the English words with their Russian equivalents.
|
1. cache memory |
a) внутренний генератор тактовых или синхронизирующих импульсов |
|
2. CMOS |
b) конвейерный режим; конвейерная обработка |
|
3. benchmark |
c) постоянно замонтированный; с фиксированным монтажом |
|
4. internal clock |
d) сверхоперативная память |
|
5. pipelining |
e) эталонный тест для проверки производительности компьютера |
|
6. hard-wired |
f) комплементарный металлооксидный полупроводник (КМОП) |
Reading.
- Read the text and try to guess the meaning of the words in bold font. Check your variants in the dictionary.
MICROPROCESSORS AND MEMORY
Microprocessor Basics
A microprocessor (or a “processor”) is an integrated circuit designed to process instructions. It is the most important component of a computer. It can be referred to as “a computer on a chip” or “a CPU on a chip” because it contains – on a single chip – circuitry that performs essentially the same tasks as the central processing unit (CPU) of a classic mainframe computer.
A microprocessor is a very complex integrated circuit, containing as many as 400 million miniaturized electronic components. The miniaturized circuitry in a microprocessor is grouped into important functional areas, such as the ALU and the control unit. The ALU (arithmetic logic unit) is the part of the microprocessor that performs arithmetic operations, such as addition and subtraction. It also performs logical operations, such as comparing two numbers to see if they are the same. The ALU uses registers to hold data that is being processed, and the microprocessor’s control unit fetches the necessary instructions. After the computer loads data into the ALU’s registers, the control unit allows the ALU to begin processing.
A microprocessor executes instructions provided by a computer program. The list of instructions that a microprocessor can perform is called its instruction set. These instructions are hard-wired into the processor’s circuitry and include basic arithmetic and logical operations, fetching data, and clearing registers. A computer can perform very complex tasks, but it does so by performing a combination of simple tasks from its instruction set.
Microprocessor Performance Factors
A microprocessor’s performance is affected by several factors, including clock speed, word size, cache size, instruction set, and processing techniques.
The microprocessor clock is a timing device that sets the pace for executing instructions. The speed of a microprocessor is usually specified in megahertz (MHz) gigahertz. A cycle is the smallest unit of time in a microprocessor’s universe. Every action a processor performs is measured by these cycles. The clock speed is not equal to the number of instructions a processor can execute in one second. In many computers, some instructions occur within one cycle, but other instructions might require multiple cycles. Some processors can execute several instructions in a single clock cycle.
Word size refers to the number of bits that a microprocessor can manipulate at one time. Word size is based on the size of registers in the ALU and the capacity of circuits that lead to those registers. A processor with a 32-bit word size, for example, has 32-bit registers, processes 32 bits at a time, and is referred to as a “32-bit processor”. Processors with a larger word size can process more data during each processor cycle that leads to increased computer performance.
Cache or “RAM cache” or “cache memory” is special high-speed memory that allows a microprocessor to access data more rapidly than from memory located elsewhere on the system board. Cache capacity is usually measured in kilobytes.
As chip designers developed various instruction sets for microprocessors, they tended to add increasingly complex instructions, each requiring several clock cycles for execution. A microprocessor with such an instruction set uses CISC (complex instruction set computer) technology. A microprocessor with a limited set of simple instructions uses RISC (reduced instruction set computer) technology. A RISC processor performs most instructions faster than a CISC processor. It might, however, require more of these simple instructions to complete a task than a CISC processor requires for the same task. Most processors in today’s personal computer use CISC technology.
Some processors execute instruction “serially” – that is, one instruction at a time. With serial processing, the processor must complete all steps in the instruction cycle before it begins to execute the next instruction. However, using a technology called pipelining, a processor can begin executing an instruction before it completes the previous instruction. Many of today’s microprocessors also perform parallel processing, in which multiple instructions are executed at the same time. Pipelining and parallel processing enhance processor performance.
Some computers have a single chip containing the circuitry for two microprocessors. A dual core processor is faster than one with a single core.
Various testing laboratories run a series of tests to gauge the overall speed of a microprocessor. The results of these tests – called benchmarks – can then be compared to the results for other microprocessors.
Random Access Memory
RAM (random access memory) is a temporary holding area for data, application program instructions, and the operating system. RAM is usually several chips or small circuit boards that plug into the system board within the computer’s system unit. RAM is the “waiting room” for the computer’s processor. It holds raw data waiting to be processed as well as the program instructions for processing that data.
RAM also holds the results of processing until they can be stored more permanently on disk or tape, it also holds data and application software instructions, operating system instructions that control the basic functions of a computer system. These instructions are loaded into RAM every time you start your computer, and they remain there until you turn off your computer.
People sometimes tend to confuse RAM and hard-disk storage, maybe because both components hold data, because they typically are “hidden” inside the system unit, or because they can both be measured in gigabytes. To differentiate between RAM and hard-disk storage, remember that RAM holds data in circuitry that’s directly connected to the system board, whereas hard-disk storage places data on magnetic media. RAM is temporary storage; hard-disk storage is more permanent. Besides, RAM usually has less storage capacity than hard-disk storage.
In RAM, microscopic electronic parts, called capacitors hold the bits that represent data. You can visualize the capacitors as microscopic lights that can be turned on and off. A charged capacitor is “turned on” and represents a”1” bit. A discharged capacitor is “turned off” and represents a “0” bit. Each bank of capacitors holds eight bits – one byte of data. A RAM address on each bank helps the computer locate data as needed, for processing.
Each RAM location has an address and uses eight capacitors to hold the eight bits that represent a byte. See Figure 1:
|
■ |
1 |
■ |
■ |
■ |
■ |
■ |
1 |
|
The two charged capacitors at the RAM address represent the letter “A” |
|
■ |
1 |
■ |
■ |
■ |
■ |
1 |
■ |
A different sequence of charged capacitors represents the letter “B” |
|
|
■ |
1 |
■ |
■ |
■ |
■ |
1 |
1 |
Another sequence of charged capacitors represents the letter “C” |
Fig. 1: The way RAM represents different characters
In some respects, RAM is similar to a chalkboard. You can use a chalkboard to write mathematical formulas, erase them, and then write an outline for a report. RAM contents can be changed just by changing the charge of the capacitors. Unlike disk storage, most RAM is volatile, which means it requires electrical power to hold data. If the computer is turned off or the power goes out, all data stored in RAM instantly and permanently disappears.
Today’s personal computer operating systems are quite adept at allocation RAM space to multiple programs. If a program exceeds its allocated space, the operating system uses an area of the hard disk, called virtual memory, to store parts of programs or data files until they are needed. By selectively exchanging the data in RAM with the data in virtual memory, your computer effectively gains almost unlimited memory capacity.
RAM components vary in speed, technology, and configuration. RAM speed is often expressed in nanoseconds or megahertz. One nanosecond (ns) is 1 billionth of a second. RAM speed can also be expressed in MHz (millions of cycles per second). Most of today’s personal computers use SDRAM (synchronous dynamic RAM), fast and relatively inexpensive, it is typically available on a small circuit board called a DIMM (dual inline memory module) or RDRAM (Rambus dynamic RAM), first developed for a game system and then adapted for use in personal computers.
Read-Only Memory
ROM (read-only memory) is a type of memory circuitry that holds the computer’s startup routine. Whereas RAM is temporary and volatile, ROM is permanent and non-volatile. ROM circuitry holds “hard-wired” instructions that are a permanent part of the circuitry and remain in place even when the computer power is turned off.
When you turn on your computer, the microprocessor receives electrical power and is ready to begin executing instructions. As a result of the power being off, however, RAM is empty and doesn’t contain any instructions for the microprocessor to execute. Now ROM plays its part. ROM contains a small set of instruction called the ROM BIOS (basic input/output system).These instructions tell the computer how to access the hard disk, find the operating system, and load it into RAM. After the operating system is loaded, the computer can understand your input, display output, run software, and access your data.
CMOS Memory
To operate correctly, a computer must have some basic information about storage, memory, and display configurations. The information is held in CMOS (pronounced “SEE moss”), a type of chip that requires very little power to hold data. It can be powered by a small battery that is integrated into the system board and automatically recharges while your computer power is on. The battery trickles power to the CMOS chip so that it can retain vital data about your computer system configuration even when your computer is turned off. When you change the configuration of your computer system, the data in CMOS must be updated.
The more data and programs that can fit into RAM, the less time your computer will spend moving data to and from virtual memory.
Comprehension check. Find the paragraph where the following ideas are found in the text.
1. It is the most significant component of the computer.
2. It executes logical operations, as well as arithmetic operations.
3. With this type of processing the processor performs one instruction at a time.
4. The results of the tests must match the results for model microprocessors.
5. If the allotted space is surpassed, the operating system employs an area of the hard disk.
6. The chip can hold the vital data about the configuration of your computer even when there is no energy supply.
Vocabulary practice
1. In the text, find the opposites to the given words.
fall short of reduce fail lose
2. Fill in the blanks choosing from the variants given.
1. CMOS memory is a type of chip that requires very little power to … data.
a) affect b) compare c) hold d) execute
2. As a result of the power being off RAM does not … any instructions for the microprocessor to execute.
a) contain b) allocate c) develop d) provide
3. The ALU uses registers to hold data as the microprocessor … arithmetic and logical operations.
a) gains b) compares c) performs d) exchanges
4. When the microprocessor receives electrical power, it is ready to begin … instructions.
a) executing b) exchanging c) allocating d) holding
5. Microprocessor instruction sets can be classified as … or … .
a) RAM or ROM b) CISC or RISC c) ROM BIOS d) CMOS memory
6. The instructions for loading the operating system into RAM when a computer is first turned on are stored in … memory.
a) RAM b) CMOS c) RISC d) ROM
7. A microprocessor (sometimes simply referred to as a “processor”) is an integrated circuit … to process instructions.
a) affected b) performed c) held d) designed
3. Make three-word expressions connected with computing combining words from three lists: A, B and C. Then fill in the gaps in the following sentences.
A: random B: system C: processor
read-only access configuration
computer core circuitry
dual memory memory
1. A … is faster than one with a single core.
2. The battery trickles power to the CMOS chip so that it can retain vital data about your … .
3. … holds the results of processing until they can be stored more permanently on disk or tape.
4. … holds “hard-wired” instructions that are a permanent part of the circuitry and remain in place even when the computer power is turned off.
4. Fill in the gaps in the text.
The microprocessor and memory are two of the most important components in a computer. The microprocessor is an integrated circuit, which is ___ to process data based on a set of instructions. The microprocessor’s ALU ___ arithmetic and logical operations. The control unit fetches each instruction, ___ it, loads data into the ALU registers, and directs all the processing activities within the microprocessor. Microprocessor performance is measured in ___ – the number of cycles per second, or clock rate. Other factors ___ overall processing speed include word size cache size, instruction set complexity, and ___.
Speaking. Discuss the following questions.
1. What exactly is a microprocessor? How does it work?
2. Where does the microprocessor get its instructions?
3. What impact does word size have on performance?
4. How does the cache size affect performance?
5. How does the instruction set affect performance?
6. What is the difference between serial processing and parallel processing?
7. How is it possible to compare microprocessor performance?
8. How does RAM differ from hard-disk storage?
9. If a computer has RAM, why does it need ROM?
10. Where does a computer store its basic hardware settings?
Text C
Pre-reading. Match the meaning of the following English words with their Russian equivalents.
|
1. storage |
a) жесткий диск |
|
2. medium |
b) резервирование; резервная копия |
|
3. read-write head |
c) темное, неотражающее пятно на поверхности CD-ROM |
|
4. pit |
d) отражающее пятно на поверхности CD-ROM |
|
5. solid state storage |
e) универсальная головка считывания – записи |
|
6. land |
f) авария (плавающих) головок |
|
7. platter |
g) контроллер, устройство управления |
|
8. head crash |
h) запоминающее устройство на монолитном носителе |
|
9. backup |
i) память, запоминающее устройство |
|
10. controller |
j) носитель; средство |
Reading. Read the text and try to guess the meaning of the words in bold font. Check your variants in the dictionary.
STORAGE DEVICES
Storage Basics
A data storage system has two main components: a storage medium and a storage device. A storage medium (storage media is the plural) is the disk, tape, CD, DVD, or other substances that contains data. A storage device is the mechanical apparatus that records and retrieves data from a storage medium. Storage devices include hard disk drives, tape drives, CD drives, and DVD drives. The term “storage technology” refers to a storage device and the media it uses.
You can think of your computer’s storage devices as having a direct pipeline to RAM. Data is copied from a storage device into RAM, where it waits to be processed. After data is processed, it is held temporarily in RAM, but it is usually copied to a storage medium for more permanent safekeeping. A computer works with data that has been coded into bits that can be represented by 1s and 0s. Obviously, the data is not literally written as “1” or “0”. Instead, the 1s and 0s must be transformed into changes in the surface of a storage medium. Exactly how this transformation happens depends on the storage technology. Three types of storage technologies are used for personal computer: magnetic, optical, and solid state.
Hard disk, floppy disk, and tape storage technologies can be classified as magnetic storage, which stores data by magnetizing microscopic particles on the disk or tape surface. Before data is stored, particles on the surface of the disk are scattered in random patterns. The disk drive’s read-write head magnetizes the particles, and orients them in a positive (north) or negative (south) direction to represent 0 and 1 bits. Data stored magnetically can be easily changed or deleted. This feature of magnetic storage provides lots of flexibility for editing data and reusing areas of a storage medium containing unneeded data. Data stored on magnetic media such as floppy disks can be altered by magnetic fields, dust, mould, smoke particles, heat, and mechanical problems with a storage device. Magnetic media gradually lose their magnetic charge, resulting in lost data. Some experts estimate that the reliable life span of data stored on magnetic media is about three years. They recommend that you refresh your data every two years by recopying it.
CD and DVD storage technologies can be classified as optical storage, which stores data as microscopic light and dark spots on the disk surface. The dark spots are called pits. The lighter, non-pitted surface areas of the disk are called lands. Optical storage gets its name because data is read using a laser light. The transition between pits and lands is interpreted as the 1s and 0s that represent data. An optical storage device uses a low-power laser light to read the data stored on an optical disk. The surface of an optical disk is coated with clear plastic, making the disk quite durable and less susceptible to environmental damage than data recorded on magnetic media. An optical disk, such as a CD, is not susceptible to humidity, fingerprints, dust, magnets, or spilled soft drinks, and its useful life is estimated at more than 30 years.
A variety of compact storage cards can be classified as solid state storage, which stores data in a non-volatile, reusable, low-power chip. The chip’s circuitry is arranged as a grid, and each cell in the grid contains two transistors that act as gates. When the gates are open, current can flow and the cell has a value that represents a “1” bit. When the gates are closed, the cell has a value that represents a “0” bit. Very little power is required to open or close the gates, which makes solid state storage ideal for battery-operated devices. Once the data is stored, it is non-volatile – the chip retains the data without the need for an external power source.
Floppy Disk Technology
Floppy disks are classified as magnetic storage because data is stored by magnetizing microscopic particles on the disk surface. A floppy disk is a round piece of flexible mylar plastic covered with a thin layer of magnetic oxide and sealed inside a protective casing.
Hard Disk Technology
Hard disk technology is the preferred type of main storage for most computer systems. A hard disk is one or more platters and their associated read-write heads. A hard disk platter is a flat, rigid disk made of aluminum or glass and coated with magnetic iron oxide particles. Hard disk platters are sealed inside the drive case or cartridge to screen out dust and other contaminants. The sealed case contains disk platters and read-write heads. Each platter has a read-write head that hovers over the surface to read data. The drive spindle supports one or more hard disk platters. Both sides of the platter are used for data storage. More platters mean more data storage capacity. Hard disk platters rotate as a unit on the spindle to position read-write heads over specific data. The platters spin continuously, making thousands of rotations per minute. Each data storage surface has its own read-write head, which moves in and out from the center of the disk to locate data. The head hovers only a few microinches above the disk surface, so the magnetic field is more compact than on a floppy disk. As a result, more data is packed into a smaller area on a hard disk platter. The density of particles on the disk surface provides hard disks with capacities far greater than floppy disks. Also, the access time for a hard disk is significantly faster than for a floppy disk.
A hard disk drive stores data at the same locations on all platters before moving the read-write heads to the next location. A vertical stack of storage locations is called a “cylinder” – the basic storage bin for a hard disk drive. A hard drive mechanism includes a circuit board called a controller that positions the disk and read-write heads to locate data. The storage technology used on many PCs transfers data from a disk, through the controller, to the processor, and finally to RAM before it is actually processed.
Hard disks are not as durable as many other storage technologies. The read-write heads in a hard disk hover a microscopic distance above the disk surface. If a read-write head runs into a dust particle or some other contaminant on the disk, it might cause a head crash, which damages some of the data on the disk. To help prevent contaminants from contacting the platters and causing head crashes, a hard disk is sealed in its case. A head crash can also be triggered by jarring the hard disk while it is in use. Although hard disks have become considerably more rugged in recent years, you should still handle and transport them with care. You should make a backup copy of the data stored on your hard disk in case of a head crash.
Tape Storage
A head crash can easily destroy hard disk data. A tape backup is a copy of the data on a hard disk, which is stored on magnetic tape and used to restore lost data. A tape backup device can simplify the task of reconstructing lost data. A backup tape can hold the entire contents of a hard disk.
CD and DVD Technology
Today, most computers are equipped with some type of optical drive – a CD drive or a DVD drive. The underlying technology for CD and DVD drives is similar, but storage capacities differ. CD and DVD drives contain a spindle that rotates the disk over a laser lens. The laser directs a beam of light toward the underside of the disk. Dark “pits” and light “lands” on the disk surface reflect the light differently. As the lens reads the disk, these differences are translated into the 0s and 1s that represent data. Optical drives use several technologies to write data on CD and DVD disks: Recordable technology (R) uses a laser to change the color in a dye layer sandwiched beneath the clear plastic disk surface. The laser creates dark spots in the dye that are read as pits. The change in the dye is permanent, so the data cannot be changed once it has been recorded. Rewritable technology (RW) uses “phase change” technology to alter a crystal structure on the disk surface. Altering the crystal structure creates patterns of light and dark spots similar to the pits and lands on a CD. The crystal structure can be changed from light to dark and back again many times, making it possible to record and modify data much like on a hard disk. Most CD drives can read CD-ROM, CD-R, and CD-RW disks, but cannot read DVDs. Most DVD drives can read CD and DVD formats.
Solid State Storage
Solid state storage is portable, provides fast access to data, and uses very little power, so it is an ideal solution for storing data on mobile devices and transporting data from one device to another. It is widely used in portable consumer devices, such as digital cameras, MP3 music players, notebook computers, PDAs, and cell phones. A USB flash drive is a portable storage device. It is durable and requires no card reader, making it easily transportable from one computer to another. You can open, edit, delete, and run files stored on a USB flash drive just as though those files were stored on your computer’s hard disk.
Comprehension check. Choose the ending for each sentence from the two versions given.
|
1. A storage device is the mechanical apparatus |
a) that hovers over the surface to read data. |
|
b) that records and retrieves data from a storage medium. |
|
|
2. After data is processed, it is held temporarily in RAM, |
a) you should still handle and transport them with care. |
|
b) but it is usually copied to a storage medium for more permanent safekeeping. |
|
|
3. Before data is stored, |
a) particles on the surface of the disk are scattered in random patterns. |
|
b) dark spots in the dye that are read as pits. |
|
|
4. Hard disk, floppy disk, and tape storage technologies can be classified as magnetic storage, |
a) making it easily transportable from one computer to another. |
|
b) which stores data by magnetizing microscopic particles on the disk or tape surface. |
|
|
5. The surface of an optical disk is coated with clear plastic, |
a) which damages some of the data on the disk. |
|
b) making the disk less susceptible to environmental damage than data recorded on magnetic media. |
|
|
6. An optical disk, such as a CD, is not susceptible to magnets, dust, humidity, |
a) and transfers data from a disk to RAM before it is actually processed. |
|
b) and its useful life is estimated at more than 30 years. |
Vocabulary practice
1. Which word does not belong to the group?
a) transportable, optical, susceptible, particle;
b) gates, retrieves, provides, handles;
c) storage, medium, magnetic, device;
d) converted, changed, transformed, stored;
e) transport, process, estimate, access;
f) disk, tape, drive, DVD;
2. Fill in the missing words choosing from the variants given.
1. A magnetic storage device uses a read-write head to magnetize … that represent data.
a) lens b) particles c) contents d) platters
2. Data on an optical storage medium, such as DVD, is stored as … and lands.
a)lands b) bits c) bytes d) pits
3. … time is the average time it takes a computer to locate data on a storage medium and read it.
a) revolution b) transporting c) valuable d) access
4. The laser creates dark spots in the dye layer that are read as … .
a) areas b) plates c) pits d) particles
5. Higher disk density provides increased storage … .
a) transformation b) capacity c) flexibility d) data
6. Hard disks are … to head crashes, so it is important to make backup copies.
a) susceptible b) optical c) retrievable d) transportable
3. Transform the following sentences without any change in meaning. Use the prompts as they are given (words in brackets, parts of sentences).
1. A storage device is the mechanical apparatus for recording and restoring data from a storage medium (retrieve).
The user … .
2. Hard disks should be operated and moved with care (handle, transport).
One … .
3. The translation of the differences between pits and lands into binary numbers is provided by the lens (translated).
The … between pits and lands into binary numbers … .
4. Revolving hard disk platters on the spindle allows the disk drive to position read-write heads over specific data (rotated).
To position read-write heads over specific data … .
5. High capacities of hard disk are available due to the high density of particles on the disk surface. (provides)
High density of particles … .
6. You can gauge hard disk drive speed in revolution per minute (pm). (to measure)
Revolution per minute … .
7. On many computers before data is actually processed, it is moved from a disk to RAM using the storage technology (processed, transfer).
Before data is actually …, … .
4. Fill in the gaps with appropriate words.
Personal computers use a variety of ___ technologies, including hard drives, CDs, DVDs, and flash drives. Each storage device essentially has a direct pipeline to a computer’s ___ so that data and instructions can move from a more permanent storage area to a temporary holding area and vice versa. Magnetic storage technology stores data by magnetizing microscopic ___ on the surface of a disk or tape. Optical storage technologies store data as a series of ___ and lands on the surface of a CD or DVD. ___ ___ storage technology stores data by activating electrons in a microscopic grid of circuitry. A standard 3.5" floppy disk for a PC stores ___ MB of data. A hard disk provides multiple ___ for data storage. Optical storage technologies, such as CD- and DVD- ___, provide good data storage capacity.
Speaking. Discuss the following questions.
1. What are the basic components of a data storage system?
2. How does a storage system interact with other computer components?
3. How does magnetic storage work?
4. How does optical storage work?
5. What are the advantages of solid state storage?
6. What is floppy disk technology?
7. How does a hard disk work?
8. What’s the downside of hard disk storage?
9. What’s the purpose of a tape drive?
10. What is the difference between CD and DVD technology?
Text D
Pre-reading. Match the meaning of the following English words with their Russian equivalents.
|
1. CRT (cathode ray tube) display |
a) жидкокристаллический дисплей |
|
2. dot pitch |
b) плата расширения |
|
3. viewing angle |
c) указательное устройство |
|
4. width |
d) шаровой указатель; шаровой манипулятор |
|
5. expansion card |
e) клавиатура |
|
6. expansion slot |
f) угол обзора |
|
7. keyboard |
g) частота регенерации; частота обновления |
|
8. LCD (liquid crystal display) |
h) кинескоп, электронно-лучевая трубка |
|
9. pixel |
i) шаг расположения точек |
|
10. pointing device |
j) пиксель, минимальный элемент изображения |
|
11. refresh rate |
k) ширина; горизонтальный размер |
|
12. trackball |
l) контактная площадка, трекпэд |
|
13. trackpad |
m) гнездо для платы |
|
14. PnP |
n) включай и работай |
Reading. Read the text and try to guess the meaning of the words in bold font. Check your variants in the dictionary.
INPUT AND OUTPUT DEVICES
Basic Input Devices
Most computer systems include a keyboard and pointing device, such as a mouse, for basic data input. Additional input devices, such as scanners, digital cameras, and graphics tablets, are handy for working with graphical input. Microphones and electronic instruments provide input capabilities for sound and music. A keyboard allows the user to key in programs and data and to control the computer system. Letters, numbers, symbols and blank spaces are known as characters. The design of most computer keyboards is based on the typewriter’s QWERTY layout (because these are the first six letters on the top left of the keyboard), which was engineered to keep the typewriter’s mechanical keys from jamming. In addition to the basic typing keypad, computer keyboards include a collection of function keys designed for computer-specific tasks, a calculator-style numeric keypad, and an editing keypad with keys such as End, Home, and Page Up.
A pointing device allows you to manipulate an on-screen pointer and other screen-based graphical controls. The most popular pointing devices for personal computers include mice, trackballs, pointing sticks, trackpads, and joysticks. A standard desktop computer includes a mouse as its primary pointing device. A mouse includes one or more buttons that can be “clicked” to input command selections. To track its position, a computer mouse uses one of two technologies: mechanical or optical. A mechanical mouse reads its position based on the movement of a ball that rolls over a mouse pad placed on a desk. An optical mouse uses an onboard chip to track a light beam as it bounces off a surface, such as a desk, clipboard, or mouse pad. An optical mouse provides more precise tracking, greater durability, less maintenance, and more flexibility to use the mouse on a wide variety of surfaces without a mouse pad. A pointing stick, looks like the top of an eraser embedded in the keyboard of a notebook computer. A trackpad is a touch-sensitive surface on which you can slide your fingers to move the on-screen pointer. A trackball looks like a mechanical mouse turned upside down. A joystick looks like a small version of a car’s stick shift and is used mostly for playing games.
Display Devices
A computer display screen is usually classified as an output device because it typically shows the results of a processing task. Some screens, however, can be classified as both input and output device because they include touch-sensitive technology that accepts input. Display devices used for output offer three technology options: CRT, LCD, and plasma. Gun-like mechanisms in the CRT (cathode ray tube) spray beams of electrons toward the screen and activate individual dots of color that form an image. CRT display devices often simply called “monitors”, are bulky, however, and consume a fair amount of power. An LCD (liquid crystal display) produces an image by manipulating light within a layer of liquid crystal cells. Modern LCD technology is compact in size and lightweight, and provides an easy-to-read display. The advantages of LCD monitors (or “flat panel displays”) include display clarity, low radiation emission, portability, and compactness. Plasma screen technology creates an on-screen image by illuminating miniature colored fluorescent light arrayed in a panel-like screen. The name “plasma” comes from the type of gas that fills fluorescent lights and gives them their luminescence. Like LCD screens, plasma screens are compact, lightweight, and more expensive than CRT monitors. They are rather energy consuming, too.
Image quality is a factor of screen size, dot pitch, width of viewing angle, refresh rate, resolution, and color depth. Screen size is the measurement in inches from one corner of the screen diagonally across to the opposite corner. The quality of a screen is often measured by the number of horizontal and vertical pixels used to create it. A pixel is a dot of color on a photo image or a point of light on a display screen. It can be in one of two modes: “on” or “off”. A larger number of pixels per square inch means a higher resolution, or clarity and sharpness of the image. The distance between one pixel on the screen and the next nearest pixel is known as dot pitch. Dot pitch (dp) is a measure of image clarity. A smaller dot pitch means a clearer image. Greater pixel densities and smaller dot pitches yield sharper images of higher resolution. A monitor’s viewing angle width indicates how far to the side you can still clearly see the screen image. A wide viewing angle indicates that you can view the screen from various positions without compromising image quality. CRT and plasma screens offer the widest viewing angles. A CRT’s refresh rate (also referred to as “vertical scan rate”) is the speed at which the screen is repainted. The faster the refresh rate, the less the screen flickers. Refresh rate is measured in cycles per second, or Hertz (Hz). The number of colors a monitor can display is referred to as color depth or “bit depth”. Most PC display devices have the capability to display millions of colors. The number of horizontal and vertical pixels that a device displays on a screen is referred to as its resolution. The resolution for many early PC displays was referred to as VGA (Video Graphics Array). Higher resolutions were later provided by SVGA (SuperVGA), XGA (eXtended Graphics Array), SXGA (Super XGA), and UXGA (Ultra XGA).
Printers
Printers are one of the most popular output devices, they usually use ink jet or laser technology. An ink jet printer has a nozzle-like print head that sprays ink onto paper to form characters and graphics. A laser printer uses the same technology as a photocopier to paint dots of light on a light-sensitive drum. Laser technology is more complex than ink jet technology, which accounts for the higher price of laser printers. A recurring cost of using a printer is the ink-jet or laser cartridge that must be replaced every few thousand pages of output. Printers differ in resolution, speed, duty cycle, operating costs, duplex capability, and memory. Printer resolution – the density of the gridwork of dots that create an image – is measured by the number of dots printed per linear inch, abbreviated as dpi, normally 900 dpi is enough. Printer speeds are measured either by pages per minute (ppm) or character per second (cps). A printer’s duty cycle determines how many pages a printer is able to process, usually measured per month (ppm). A printer with duplex capability can print on both sides of the paper, though it will slow down the print process. A computer sends data for a printout to the printer along with a set of instructions on how to print that data. Printer Control Language (PCL) is the most widely used language for communication between computers and printers, but PostScript is an alternative printer language that many publishing professionals prefer. The data that arrives at a printer along with its printer language instructions requires memory.
Installing Peripheral Devices
Today, many peripheral devices connect to an external USB (universal serial bus) port and Windows automatically loads their service drivers, making installation as simple as plugging in a table lamp. USB is currently the most popular technology for connecting peripherals.
USB ports are conveniently located on the front of the system unit for easy access. When you install a peripheral device, you are creating a connection for data to flow between the device and the computer. Within a computer, data travels from one component to another over circuits called a data bus. One part of the data bus runs between RAM and the microprocessor. Other parts of the data bus connect RAM to various storage and peripheral devices. The segment of the data bus that extends between RAM and peripheral devices is called the expansion bus. As data moves along the expansion bus, it can travel through expansion slots, cards, ports, and cables. An expansion slot is a long, narrow socket on the system board into which you can plug an expansion card. An expansion card is a small circuit board that gives a computer the capability to control a storage device, an input device, or an output device. Expansion cards are also called “expansion boards”, “controller cards”, or “adapters”. Expansion cards are built for only one type of slot. An expansion port is any connector that passes data in and out of a computer or peripheral device. Built in ports supplied with a computer usually include a mouse port, keyboard port, serial port, and USB ports. Most notebook computers are equipped with several USB ports.
Some devices require software, called a device driver, to set up communication between your computer and the device. The directions supplied with your peripheral device include instructions on how to install the device driver. Typically, you use the device driver disk or CD one time to get everything set up, and then you can put the disk away in a safe place. Installing a peripheral device you should remember that the cable you use must match the peripheral device and a port on the computer. If the right type of port is not available, you might have to add an expansion card. Once the connection is made, PnP should recognize the new device. If not, you will probably have to install driver software.
Comprehension check. Match the beginnings of the sentences in the first column with the endings in the second.
|
A |
B |
|
1. In addition to the basic typing keypad, computer keyboards include a collection of function keys |
a) it can travel through expansion slots, cards, ports, and cables. |
|
2. A pointing device allows you |
b) to use the mouse on a wide variety of surfaces without a mouse pad. |
|
3. A recurring cost of using a printer is the ink-jet or laser cartridge |
c) designed for computer-specific tasks. |
|
4. An optical mouse provides more precise tracking, less maintenance, and more flexibility |
d) to manipulate an on-screen pointer and other screen-based graphical controls. |
|
5. As data moves along the expansion bus, |
e) that offers an inexpensive and dependable way of output. |
|
6. A CRT (cathode ray tube) display is a device |
f) that must be replaced every few thousand pages of output. |
Vocabulary practice
1. Fill in the blanks in the sentences with the necessary word(s); all the letters of the word(s) are given on the right.
|
1. Some … are designed to avoid wrist and injures caused by hours of keyboarding. |
OAYEDSBKR |
|
2. Certain input devices record and … the sound of the human voice into … signals. |
TRNVOEC TIIGDLA |
|
3. Some input systems … a computer to understand a voice it has never heard. |
WOLLA |
|
4. The first generation of digital cameras could create photos with … of 650 x 480 pixels. |
ULOOESRNTI |
|
5. An optical mouse requires less …; you can … it on any kind of surface. |
EANEACINNTM EANALMPIUT |
|
6. Even a steady image on a monitor is constantly regenerated, or …, from top to bottom. |
DEEFHRRES |
2. Fill in the missing words choosing from the variants given.
a) viewing angle b) pixel c) resolution d) surface
e) allows f) pitches g) display
1. A keyboard … the user to key in programs and data and to control the computer system.
2. An optical mouse uses an onboard chip to track a light beam as it bounces off a …, such as a desk, clipboard, or mouse pad.
3. Some … screens, can be classified as both input and output devices.
4. Greater … densities and smaller dot … yield sharper images of higher resolution.
5. A wide … indicates that you can view the screen from various positions without compromising image quality.
6. Printer … is measured by the number of dots printed per linear inch.
3. Match the beginnings and the endings of the statements given and put the sentences you get into the correct order.
|
1. Once the connection is made, |
a) you’ll probably have to install driver software. |
|
2. You have to use the expansion bus |
b) must match the peripheral device and a port on the computer. |
|
3. If you want to install a peripheral device |
c) to recognize just any peripheral device automatically. |
|
4. If it does not, |
d) PnP will recognize the new device. |
|
5. If the right type of port is not available, |
e) you need PnP. |
|
6. PnP is a feature that allows the computer |
f) you might have to add an expansion card. |
|
7. The cable you use |
g) to make a connection between the system board and a peripheral device. |
4. Fill in the gaps in the text with appropriate words.
Most computer systems include a keyboard and some type of ___ device for basic data input. A mouse is standard equipment with most desktop computer systems. For output, most computers include a display device. A ___ produces an image by spraying electrons toward the screen. ___ technology produces an image by manipulating light within a layer of liquid crystal cells. ___ screen technology creates an on-screen image by illuminating miniature fluorescent lights arrayed in a panel-like screen. Image quality for a display device is a factor of screen size, ___ ___, ___ of viewing angle, resolution, refresh rate, and color ___.
Speaking. Discuss the following questions.
1. What devices are used to get data into a computer?
2. What does a pointing device do?
3. What options are for output devices?
4. Which display technology produces the best image?
5. What printer technologies are most popular with personal computer users?
6. What are the operating characteristics of a printer?
7. How does a computer move data to and from peripheral devices?
8. What is an expansion slot? What is an expansion card used for?
9. What is an expansion port? What are other names for it?
10. Why do some peripheral devices include a disk or CD?
Critical Thinking. Read the article and express you opinion on the problem.
Computers and the Environment
According to a United Nations study, producing a computer is more materials-intensive than manufacturing an automobile. Extending the lifespan of your computer might be environmentally friendly, but keeping up with technology probably means replacing your computer every few years. When it is time to replace your computer, is there a way to do it in an environmentally safe way? In this world of rapidly changing technology, disposal of computers and other electronic equipment has created a new and growing waste stream. In the United States alone, almost eight printer cartridges are discarded every second. Landfills hold millions of tons toxic substances such as lead, cadmium and mercury.
Is it worth recycling obsolete computers? Then the question arises: Who pays? Should it be the taxpayer, the individual consumer, the retailer, or the computer manufacturer? Consumers buying computers in California, have to pay a recycling fee at the time of purchase. Maryland requires computer manufacturers to ante up an annual fee for electronic waste disposal. Some manufacturers provide their customers with a postage-paid shipping box so they can return the product for recycling. In Europe, legislation proposes to make manufacturers accept returns of their old equipment free of charge and take appropriate steps to recycle it.
Having no or vague laws, consumers are often confused about how to dispose of their unwanted computers, monitors, CDs, and ink cartridges.
What do you think?
1. Have you ever thrown away an old computer or other electronic device?
2. Are you aware of any option for recycling electronic equipment in your area?
3. Would it be fair for consumers to pay a recycling tax on any electronic
equipment that they purchase?
Final Test. Do the tasks in the following test.
1. ___ is permanent, non-volatile, typically used to store a computer’s startup routine.
a) RAM b) ROM c) CMOS d) SDRAM
2. ___ storage devices store data in a non-volatile, erasable, low-power chip.
a) optical b) magnetic c) solid state d) none of the above
3. RAM is considered to be volatile memory because ___.
a) it sporadically loses information b) it requires electrical power to hold data
c) data stored in it can randomly duplicate itself d) it’s measured in GB
4. Data stored in a special high-speed memory, called ___, can be accessed more rapidly than data from memory located elsewhere on the system board.
a) clock speed b) word size c) cache d) instruction set
5. All of the following are examples of storage medium except ___.
a) a CD b) paper c) a keyboard d) a DVD
6. Storage device that stores data as pits and lands is referred to as ___.
a) tape b) floppy disk c) CD-ROM d) hard drive
7. 1s and 0s are referred to as ___ digits.
8. An expansion ___ is any connector that passes data in and out of a computer or peripheral device.
9. Many of today’s microprocessors use ___ processing, which allows them to execute multiple instructions at the same time.
10. A ___ circuit is also known as a computer chip or microchip. It is a very thin slice of semi-conducting material packed with microscopic circuit elements.
11. Prior to processing data is copied from a storage device into ___.
12. Every action that is performed by a microprocessor is measured in ___, the smallest unit of measurement used by microprocessors.
13. ___ in RAM are microscopic electronic parts that hold the bits that represent data.
14. The word “bit” and the lowercase letter “b” are abbreviations for “binary___”.
15. The ROM ___ is a set of instructions which tells the computer how to access the hard disk, find the operating system, and load the operating system into RAM.
16. The ___ for a machine code instruction specify the data for the operation.
17. Data travels from one component to another over circuits called a data ___.
18. The process of retrieving data from a storage medium is referred to as “___ data” or “opening a file”.
19. Data which is composed of letters, symbols, and numerals that is not used in arithmetic operations is called ___ data.
20. The two main components of a storage system are a storage device and a ___.
Projects. Choose and perform one of the projects given.
1. Write a two- to five-page paper about recycling computers. To begin this project, consult the text from Critical Thinking. Then determine the specific aspect of the issue you will present in your paper. You might, for example, decide to focus on toxic materials that end up in landfills or barriers that discourage shipping old computers across national borders. Whatever aspect of the issue you present, make sure you can back up your discussion with facts and references to authoritative articles and Web pages.
2. Work in groups of three or four. Select a digital device (e.g. a printer, scanner, digital camera, digital music player, etc.), and create promotional materials for a tradeshow booth featuring your “product”. You might include a product photo, list of specifications, a short instruction manual. Present your sales pitch or demonstration to the rest of the class.
Unit 3. COMPUTER SOFTWARE
Text A
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
SOFTWARE BASICS
Software: the inside story
Computer software determines the types of tasks a computer can help you accomplish. Some software helps you create documents; while other software helps you edit home videos, prepare your tax return or design the floor plan for a new house.
The instructions that tell a computer how to carry out a task are referred to as a computer program. These programs form the software that prepares a computer to do a specific task, such as document production, video editing, graphic design or Web browsing. In popular usage the term “software” refers to one or more computer programs and any additional files that are provided to carry out a specific type of task. Whether it’s on a CD or downloaded from the Web, today’s software is typically composed of many files. You might be surprised by the number of files that are necessary to make software work. At least one of the files included in a software package contains an executable program designed to be launched, or started, by users. On PCs, these programs are stored in files that typically have .exe file extensions and are referred to as “executable files”. Other files supplied with a software package contain programs that are not designed to be run by users. These “support programs” contain instructions for the computer to use in conjunction with the main user-executable file. A support program can be activated by the main program as needed. Support programs often have file extensions such as .dll and .ocx.
In addition to program files, many software packages also include data files. As you might expect, these files contain any data that is necessary for a task, but not supplied by the user, such as Help documentation. The data files supplied with a software package sport files extensions such as .txt, .bmp, and .hlp. (see fig. 2):
The use of a main user-executable file plus several support programs and data files offers a great flexibility and efficiency for software developers. Support programs and data files from existing programs can usually be modified by developers for other programs without changing the main executable file. This modular approach can reduce the time required to create and test the main executable file, which usually contains a long and fairly complex program. This modular approach also allows software developers to reuse their support programs in multiple software products and adapt preprogrammed support modules for use in their own software. Modular programming techniques are of interest mainly to people who create computer programs; however these techniques affect the process of installing and uninstalling software. It is important, therefore, to remember that computer software consists of many files that contain user-executable programs, support programs, and data.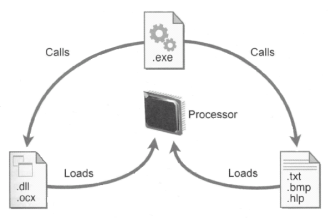
Programmers and programming languages
Computer programmers write computer programs that become the components of a computer software product. The finished software product is then distributed by the programmers or by software publishers– companies that specialize in marketing and selling software. Today most businesses and organizations purchase commercial software to avoid the time and expense of writing their own.
Most software provides a task-related environment, which includes a screen display, a means of collecting commands and data from the user, the specifications for processing data, and a method for displaying or outputting data. To create a software environment, a programmer must define properties for each element in the environment, such as where the objects appear, its shape, color and behavior.
A programming language provides the tools a programmer uses to create software and produce a lengthy list of instructions, called source code, which defines the software environment in every detail – what it looks like, how the user enters commands, and how it manipulates data. Most programmers today prefer to use a high-level language, such as C++, Java, Ada, COBOL, or Visual Basic. These languages have some similarities to human languages and produce programs that are fairly easy to test and modify.
A computer’s microprocessor understands only machine language – the instruction set that is “hard wired” within the microprocessor’s circuits. Therefore, instructions written in a high-level language must be translated into machine language before a computer can use them. The process of translating instructions can be accomplished by two special types of programs: compilers and interpreters. A compiler translates all the instructions in a program as a single batch, and the resulting machine language instructions, called object code, are placed in a new file. Most of the program files on a distribution CD for commercial software are compiled so that they contain machine language instructions that are ready for the processor to execute. As an alternative to a compiler, an interpreter converts one instruction at a time while the program is running. An interpreter reads the first instruction, converts it into machine language, and then sends it to the microprocessor. After the instruction is executed, the interpreter converts the next instruction, and so on.
Software is categorized as application software or system software. The primary purpose of application software is to help people carry out tasks using a computer. In contrast, the primary purpose of system software – your computer’s operating system, device drivers, programming languages, and utilities – is to help the computer to carry out its basic operating functions.
Software can be classified into categories (see fig. 3):




![]()




![]()
![]()
![]()
![]()
![]()




![]()
![]()

Fig. 3: Software categories
Comprehension check. Mark the following statements as True or False.
1. Computer software typically consists of many files that contain user-executable programs, support programs and data files.
2. The main executable file provides the primary set of instructions for the computer to execute and calls various support programs and data files as needed.
3. Support programs often have file extensions such as .txt, .bmp, and .hlp.
4. Individuals often write software for their personal computers.
5. High-level languages are fairly easy to test and modify.
6. A compiler converts high-level instructions into a new file containing machine language instructions.
Vocabulary practice
1. In the text find the synonyms to the given words.
start a program objective define method decrease provide perform
2. Fill in the blanks choosing from the variants given.
1. The instructions that tell a computer how to … a task are referred to as a computer program.
a) require b) create c) carry out d) define
2. A programming language … tools for creating a lengthy list of instructions called source code.
a) prefer b) refer to c) avoid d) provide
3. As a program is running an interpreter converts one instruction… into machine language.
a) at a time b) at the same time c) all the time
4. eVidpro.exe is a compiled program, so its instructions are immediately … by the processor.
a) provided b) modified c) executed d) adapted
5. Software includes menus, buttons, and other control objects that are … by a programmer, who designates their properties.
a) converted b) defined c) reduced d) purchased
6. The software that provides the computer with … for each use is called application software.
a) approaches b) efficiency c) utilities d) instructions
3. Make two-word expressions by combining words from two lists: A and B. Then fill in the gaps in the following sentences.
A: executable B: language
application code
machine file
source extensions
file software
high-level instructions
1. When using a Windows PC, you can start an … by clicking its icon, selecting it from a Start menu, or entering its name in the Run dialog box.
2. Computer software can be divided into two major categories: … software and system software.
3. The data files supplied with a software package sport … such as .txt, .bmp, .hlp.
4. A programming language provides tools for creating a lengthy list of instructions called … .
5. A simple instruction to add two numbers becomes a long series of 0s and 1s in a… .
6. A compiler converts … into a file containing machine language instructions.
4. Fill in the gaps in the text.
Software consists of computer ___ (programs/utilities) and data files that work together to provide a computer with the ___ (instructions/approaches) and ___ (data/tools) necessary for carrying out a specific type of task, such as document production, video editing, graphic design, or Web browsing.
To create a software ___ (efficiency/environment), a programmer must define the ___ (approaches/properties) for each element in the environment, such as where an object appears, its shape, its color, and its behavior. Most programmers today prefer to use ___ (high-level/machine) languages. A computer’s microprocessor understands only ___ (machine/high-level) language, however, so a program that is written in a high-level language must be ___ (avoided/compiled) or interpreted before it can be ___ (processed/modified).
Speaking. Discuss the following questions.
1. What is software?
2. What kinds of files are included in a typical software product?
3. Why does software require so many files?
4. How does a programmer “write” software?
5. How does a computer process a program?
6. How is software categorized?
Text B
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
OPERATING SYSTEMS AND UTILITIES
Operating system overview
An operating system (abbreviated OS) is a type of system software that acts as a mast controller for all the activities that take place within a computer system. It is one of the factors that determine your computer compatibility and platform. The operating system interacts with application software, device drivers, and hardware to manage a computer’s resources. The term resource refers to any component that is required to perform work. For example, the processor is a resource. RAM, storage space, and peripherals are also resources.
Operating system manages different tasks:
- Manage memory. OS allocates a specific area of RAM for each program that is open and running. OS is itself a program, so it requires RAM space too. A microprocessor works with data and executes instructions stored in RAM – one of your computer’s most important resources. When you want to run more than one program at a time, the OS has to allocate specific areas of memory for each program. When multiple programs are running, the OS must ensure that instructions and data from one area of memory do not “leak” into an area allocated to another program. If an OS falls down on the job and fails to protect each program’s memory area, data can get corrupted, programs can “crash”, and your computer displays error messages.
- Manage processor resources. The operating system also controls the microprocessor – just at a slightly higher level. Every cycle of a computer’s microprocessor is a resource for accomplishing tasks. Many activities – called “processes” – compete for the attention of your computer’s microprocessor. OS must ensure that each activity “process” receives its share of microprocessor cycles. A computer can take advantage of performance-enhancing technologies such as multitasking, multithreading, multiprocessing, dual core or multiple processors.
- Keep track of storage resources. OS stores and retrieves files from your disks and CDs. It remembers the names and locations of all your files and keeps track of empty spaces where new files can be stored.
- Ensure that input and output proceed in an orderly manner. OS communicates with device driver software so that data can travel smoothly between the computer and these peripheral resources. OS uses ‘buffers’ to collect and hold data while the computer is busy with other tasks.
- Establish basic elements of the user interface. A user interface can be defined as the combination of hardware and software that helps people and computers communicate with each other. Your computer’s user interface includes a display device, mouse, and keyboard that allow you to view and manipulate your computer environment. It also includes software elements, such as menus and toolbar buttons. A graphical user interface (GUI) features menus and icons that you can manipulate with the click of a mouse. A command-line interface requires you to memorize and type commands.
For nearly all PCs, servers, workstations, mainframes, and supercomputers, the operating system program is quite large, so most of it is stored on a hard disk. The operating system’s small bootstrap program is stored in ROM and supplies the instructions needed to load the operating system’s core into memory when the system boots. This core part of OS called the kernel provides the most essential operating system services, such as memory management and file access. The kernel always stays in RAM all the time your computer is on. Other parts of OS, such as customization utilities, are loaded into RAM as they are needed.
Many operating systems provide helpful tools, called operating system utilities, that you can use to control and customize your computer equipment and work environment. They are typically accessed by using a GUI, such as the familiar Windows desktop. The most popular are: launch programs, manage files, get help, customize the user interface, and configure equipment.
One operating system might be better suited to some computing tasks than others. To provide clues to their strengths and weaknesses, operating systems are informally categorized using one or more of the following terms:
A single-user operating system expects to deal with one set of input devices – those that can be controlled by one user only.
A multiuser operating system allows a single computer to deal with simultaneous input, output, and processing requests from many users. One of its most difficult responsibilities is to schedule all the processing requests that a centralized computer must perform.
A network operating system provides communications and routing services that allow computers to share data, programs, and peripheral devices. The main difference between network OS and multiuser OS is that multiuser operating systems schedule requests for processing on a centralized computer, whereas a network operating system simply routes data and programs to each user’s local computer, where the actual processing takes place.
A desktop operating system is one that is designed for a personal computer. Typically, these operating systems are designed to accommodate a single user, but might also provide network capability.
Windows is the best-selling operating system. The number and variety of programs that run on Windows are unmatched by any other operating system, a fact that contributes to its dominant position as the most widely used desktop operating system.
Utility software is a type of system software that is designed to perform a specialized task, such as system maintenance or security. Utility software that does not come packaged with an operating system is often referred to as a third-party utility. In past years, antivirus software was a popular category of third-party utilities. With the recent influx of nuisance ads, intrusion attempts, and spam, utilities such as ad blockers, personal firewalls, and spam filters have also become best sellers. Filtering software is used by parents to block their children from objectionable Websites. Another popular category of utility software is system utilities. These utilities track down and fix disk errors, repair corrupted files, and give your PC a performance – enhancing tune-up.
A final group of utilities worth mentioning is designed for backing up and cleaning up hard disks, and shredding files so they can’t be recovered. They can help you recover files deleted by mistake.
Comprehension check. Indicate the paragraph where the following ideas are found in the text.
1. Operating system’s main purpose is to control what happens behind the scene.
2. Your PC can sometimes recover from memory leak problems if you use the Ctl+Alt+Del key sequence to close the corrupted program.
3. The operating system must ensure that the microprocessor does not “spin its wheels” waiting for input while it could be working on some other processing projects.
4. Windows is installed on more than 80 % of the world’s personal computers.
5. The term “buffer” is a technical jargon for a region of memory that holds data waiting to be transferred from one device to another.
6. Many operating systems provide helpful tools, called operating system utilities, that you can use to control and customize your computer equipment and work environment.
Vocabulary practice
1. In the text find the opposites to the given words.
roughly shred disorganize monopolize stop succeed break
2. Fill in the blanks choosing from the variants given.
1. An operating system … a computer’s resources, such as Ram, storage space, and peripherals.
a) allocates b) defines c) manages d) accommodates
2. To … more than one program at a time, the operating system must allocate specific areas of Ram for each program.
a) store b) install c) fix d) run
3. A graphical user-interface provides a way to point and click a mouse to … menu options and manipulate objects that appear on the screen.
a) feature b) deal with c) select d) manage
4. Handheld devices, such as PDAs and smartphones typically … single-user operating systems.
a) feature b) retrieve c) include d) establish
5. OS communicates with device driver software so that data can travel … between the computer and peripheral resources.
a) roughly b) smoothly c) simultaneously d) primary
6. Desktop operating systems are designed to accommodate a single user, but might also provide network … .
a) variety b) security c) capability d) compatibility
3. Make three-word combinations using the words in columns and then fill in the gaps in the following sentences.
A: multiuser B: operating C: system
third user technologies
desktop enhancing interface
graphical operating system
performance party utilities
1. IBM’s OS/390 is one of the most popular mainframe … .
2. A computer can take advantages of … .
3. A … features menus and icons that you can manipulate with a click of a mouse.
4. A …, such as Windows, is designed for personal computers.
5. WinZip, WinAce are … that offer a variety of compression options.
4. Fill in the gaps in the text.
___ (computer/application) software tells the operating system what to do. The operating system tells the ___ (device/tool) drivers, device drivers tell the ___ (software/hardware), and the hardware actually does the work. The operating system___ (interacts/competes) with application software, device drivers, and hardware to ___ (manage/define) a computer’s ___ (resources/compatibility).
The core part of an operating system is called the ___ (kernel/cycle). In addition to this core, many operating systems ___ (provide/schedule) helpful tools, called ___ (utilities/capabilities).
Speaking. Discuss the following questions.
1. What is an operating system?
2. What does an operating system do?
3. How does an operating system manage processor resources?
4. Why does an operating system manage memory?
5. Where is the operating system stored?
6. What are utilities? What are the most popular ones?
7. How does the operating system affect the user interface?
Text C
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
APPLICATION SOFTWARE
Most computers include some basic word processing, e-mail, and Internet access software, but computer owners want additional software to increase their computer’s productivity, business, learning, or entertainment capabilities.
Document production software
This software assists you with composing, editing, designing, printing, and electronically publishing documents. The three most popular types of document software are word processing, desktop publishing, and Web authoring.
Word processing software, such as Microsoft Word gives you the ability to create, spell-check, edit, and format a document on the screen before you commit it to paper.
Desktop publishing software (abbreviated DTP) has sophisticated features to help you produce professional-quality output for newspapers, newsletters, brochures, magazines, and books.
Web authoring software helps you design and develop customized Web pages that you publish electronically on the Internet. It provides easy-to-use tools for composing the text for a web page, assembling graphical elements, and automatically generating HTML tags.
Document production software makes it easy to let your ideas flow because it automatically handles many tasks as “word wrap”, a spelling checker. It offers several features that can improve the quality of your writing. They are: a thesaurus, a grammar checker, a readability formula, a Search and Replace. The “look” of your final document depends on several formatting factors, such as font style, paragraph style, and page layout. Document production software allows you to work more productively.
Spreadsheet Software
A spreadsheet uses rows and columns of numbers to create a model or representation of a real situation. Today, spreadsheet software, such as Microsoft Excel, provides tools to create electronic spreadsheets. As an added bonus, spreadsheet software helps you turn your data into a variety of colorful graphs. It also includes special data-handling features that allow you to sort data, search for data that meets specific criteria, and print reports. Spreadsheets are popular with accountants and financial managers who deal with paper-based calculations. Because it is easy to experiment with different numbers, spreadsheet software is particular useful for what-if analysis. The disadvantage of spreadsheet software is that – aside from a few predesigned templates – you are responsible for entering formulas and selecting functions for calculations. If you don’t know the formulas or don’t understand the functions, you are out of luck.
In contrast to spreadsheet software, “number crunching” software provides a structured environment dedicated to a particular number crunching tasks, such as statistical analysis, mathematical modeling, or money management.
Database Software
A database is simply a collection of data that is stored on one or more computers. It can contain any sort of data. Database software helps you enter, find, organize, update, and report information stored in a database. Microsoft Access, FileMaker Pro, and ask Sam are three of the most popular examples of database software for personal computers. Database software stores data as a series of records, which are composed of fields that hold data. A record holds data for a single entity – a person, place, or event. A field holds one item of data relevant to a record. Your database software can help you print reports, export data to other programs, convert the data to other formats such as HTML.
Whether you print, import, copy, save, or transmit the data you find in databases, it is your responsibility to use it appropriately. Never introduce inaccurate information into a database.
Graphics Software
Graphics software is designed to help you create, manipulate, and print graphics. Some graphics software products specialize in a particular type of graphic, while others allow you to work with multiple graphics formats. If you are really interested in working with graphics, you will undoubtedly end up using more than one graphics software product. The most popular are paint software, photo editing software, and drawing software, CAD (computer-aided design) software, and presentation software.
Video editing software provides a set of tools for transferring video footage from a camcorder to a computer, clipping out unwanted footage, assembling video segments in any sequence, adding special visual effects, and adding a sound track. DVD authoring software offers tools for creating DVD with Hollywood-style menus.
A software suite is a collection of application software sold as a single package.
Educational software helps you learn and practice new skills. It is available for such diverse educational endeavors as learning languages, training yourself to use new software, how to play the piano or guitar, and improving keyboarding skills. Exam preparation software is available for standardized tests.
Reference software provides a collection of information and a way to access that information. This type of software includes massive amount of data. The reference software category spans a wide range of applications – from encyclopedias to medical references, from map software to trip planners, and from cookbooks to telephone books. The options are as broad as the full range of human interests.
Computer games are the most popular type of entertainment software. Music software is represented by audio editing software, CD ripper software, audio encoding software, ear training software.
Comprehension check. Choose the ending for each sentence from the two versions given.
1. You can vary the font style selecting character formatting attributes, such as
a) italics, bold, underline, etc. b) layout, headers, frames, etc.
2. A thesaurus can help you find
a) opposites for a word. b) synonyms for a word.
3. In a worksheet,
a) each column is numbered and each row is lettered.
b) each column is lettered and each row is numbered.
4. Mathematical modeling software helps you
a) visualize the product of complex formulas.
b) analyze large sets of data to discover patterns.
5. Database software helps you
a) learn and practice new skills. b) enter and organize information.
6. A software suite is
a) a collection of application software sold as a single package.
b) a collection of data stored on one or more computers.
Vocabulary practice
1. Which word does not belong to the group?
a) assist, help, edit, aid;
b) contain, select, choose, pick;
c) relevant, additional, supplementary, extra;
d) spreadsheet, database, Linux, graphics;
e) handle, deal with, assemble, manage;
f) generate, update, form, create.
g) improve, search for, upgrade, enhance
2. Fill in the missing words choosing from the variants given.
1. Various kinds of document product software provide tools for creating and … printed and web-based materials.
a) formatting b) sorting c) assembling d) transmitting
2. Spreadsheet software provides a sort of “blank canvas” on which you can create numeric … by simply “painting” values, labels, and formulas.
a) columns b) sequences c) models d) features
3. Database software stores data as a series of … and allows you to establish relationships between different types of records.
a) templates b) items c) entities d) records
4. CD ripper software … files from an audio CD to your computer’s hard disk.
a) edits b) transfers c) formats d) sorts
5. DVD authoring software … you to add Hollywood style menus to digital videos.
a) lets b) makes c) allows d) helps
6. The reference software category spans a wide … of applications.
a) entity b) sequence c) range d) circuit
3. Transform the following sentences without any change in meaning. Use the prompts as they are given (words in brackets, parts of sentences).
1. Most document production software includes a spelling checker.
A spelling checker is mostly …
2. Word processing offers several features that can improve the quality of writing (to enhance).
3. You may not be a composer or a musician to have a use for music software.
Neither … nor …
4. Many types of CAD software is available (get access).
5. Instead of typing data into a database you can also use data from a commercial database (import).
… than … you can …
6. If you are interested in working with graphics, you end up using more than one graphics software product (combine).
One who …
4. Fill in the gaps in the text.
The three most popular types of document production software include word processing, ___, and Web authoring. ___ software is similar to a “smart” piece of paper that automatically adds up the ___ of numbers you write on it. You can use it to make other calculations, too, based on simple equations that you write or more complex, built-in ___. Because it’s so easy to experiment with different numbers, this type of software is particular useful for ___ analyses. ___ software helps you store, find, organize, update, and report information stored in one or more tables. When two sets of records are ___, database software allows you to access data from both tables at the same time. A software ___ is a “bundled” collection of application software sold as a single package.
Speaking. Discuss the following questions.
1. How does document production software help me turn my ideas into sentences and paragraphs?
2. What if I am a bad speller?
3. What features of document product software can improve my writing?
4. What is a spreadsheet?
5. What other “number-crunching” software is available?
6. What is a database?
7. What is the best –selling entertainment software?
8. What is a software suite?
Text D
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
BUYING AND INSTALLING SOFTWARE
It’s surprising how quickly your collection of software can grow as you discover new ways to use your computer. Before you can use software, you have to install it on your computer.
The key “ingredients” necessary to install new software are the files that contain the programs and data. These files might be supplied on distribution media. System requirements, which specify the operating system and minimum hardware capacities necessary for a software product to work correctly can be found on the software box or posted on the download site.
Installation basics
When you install software, the new software files are placed in the appropriate folders on your computer’s hard disk, and then your computer performs any software or hardware configurations necessary to make sure the program is ready to run. During the installation process, your computer usually performs the following tasks:
- Copies files from distribution media or downloads files to specified folders on the hard disk
- Uncompresses files that have been distributed in compressed format.
- Analyzes the computer’s resources, such as processor speed. RAM capacity, and hard disk capacity, to verify that they meet or exceed the minimum system requirements.
- Analyzes hardware components and peripheral devices to select appropriate device drivers.
- Looks for any system files and players, such as Internet Explorer or Windows media Player, that are required to run the program but are not supplied on the distribution media or download.
- Updates necessary system files, such as the Windows Registry and the Windows Start menu, with information about the new software.
Software updates
Software publishers regularly update their software to add new features, fix bugs, and update its security. Types of software updates (also called “upgrades”), include new versions, patches, and service packs. A software patch is a small selection of program code that replaces part of the software you currently have installed. The term service pack, which usually applies to operating system updates, is a set of patches that correct problems and address security vulnerabilities. Software patches and service packs are usually free. It’s always a good idea to install patches and services when they become available. The revised code they contain often addresses security vulnerabilities and the sooner you patch up those holes, the better. A new version update usually installs in a similar way as you installed the original version, by activating a setup program, displaying a license agreement, and adding updated entries to your computer’s Start menu. Patches and service packs are usually distributed over the Internet and automatically install themselves when you download them. To combat piracy, many software publishers require users to type in a validation code to complete an installation. The result of an update depends on several factors. Most patches and service pack installations can not be reversed. A new version installation typically overwrites the old version, but you might have the option to keep the old version just in case you have trouble with the new one and need to revert back to the previous version.
Uninstalling software
With some operating systems, such as DOS, you can remove software simply by deleting its files. Other operating systems, such as Windows and Mac OS, include an uninstall routine, which deletes the software’s files from various folders on your computer’s hard disk. The uninstall routine also removes references to the program from the desktop and from operating system files, such as the file system restrictions.
Software Copyrights and licenses
Copyright laws have fairly severe restrictions on copying, distributing, and reselling software; however, a license agreement might offer additional rights to consumers. The licenses for commercial software, shareware, freeware, open source, and public domain software specify different levels of permission for software use, copying, and distribution.
Commercial software is typically sold in computer stores or at Web sites. Although you “buy” this software, you actually purchase only the right to use it under the terms of the software license.
Shareware is copyrighted software marketed under a “try before buy” policy. It typically includes a license that permits you to use software for a trial period. To use it beyond the trial period you must pay a registration fee. A shareware license usually allows you to make copies of the software and distribute them to others. If they choose to use the software, they must pay a registration fee as well.
Freeware is copyrighted software that is available for free. Because the software is protected by copyright, you cannot do anything with it that is not allowed by copyright law or by the author. Typically, the license for freeware permits you to use the software, copy it, and give it away, but does not permit you to alter it or sell it. Many utility programs, device drivers, and some games are available as freeware.
Open source software makes the uncompiled program instructions – the source code – available to programmers who want to modify and improve the software.
Public domain software is not protected by copyright because the copyright has expired, or the author has placed the program in the public domain, making it available without restriction. It may be freely copied, distributed, even resold. The primary restriction on public domain software is that you are not allowed to apply for a copyright on it.
Comprehension check. Match the beginnings of the sentences in the first column with the endings in the second.
|
1. When you install software its files |
for different operating systems. |
|
2. Installation procedures differ |
might end up in different folders. |
|
3. Downloadable software can be provided |
that guides you through the installation process. |
|
4. Public domain software |
involves a fee. |
|
5. Windows software typically contains a setup program |
in several different formats . |
|
6. Updating to a new version usually |
is not protected by copyright. |
Vocabulary practice
1. Put the letters in the following words into correct order.
tchopgiry roeisttcri deexec susnecropm trneeqmueir rdeivsoc erceneefr
2. Fill in the blanks choosing from the variants given.
1. System … specify the operating system and minimum hardware capacities required for software to work correctly.
a) requirements b) references c) replacements
2. During the … process, your computer performs many tasks, including updating the Windows Registry and Start menu.
a) uninstallation b) installation c) updating d) copyrighting
3. Linux is an example of … software.
a) open source b)freeware c) public domain d) shareware
4. A software patch is a small selection of program code that … part of the software you currently have installed.
a) activates b) replaces c) installs d) specifies
5. Public domain software is not copyrighted because the copyright has … .
a) completed b) expired c) replaced d) purchased
6. Software patches and service packs are usually … .
a) expensive b) inexpensive c) free
3. Restore the instructions for installing software from distribution media by matching the beginnings with the endings and put them into the correct order.
|
Start |
the license agreement if one is presented on the screen. By agreeing to the terms of the license, you can proceed with the installation. |
|
Insert |
the first distribution CD or DVD. The setup program should start automatically. |
|
Select |
the prompts provided by the setup program to specify a folder to hold the new software program. |
|
Follow |
the installation option that best meets your needs. |
|
Read |
the program you just installed to make sure it works. |
|
Insert |
multiple distribution CDs in the specified drive when the setup program prompts you. |
4. Fill in the gaps in the text.
When you ___ software, the new software files are placed in the appropriate ___ on your computer’s hard disk, and then your computer performs any software configurations that are necessary to make sure the program is ready to run. The ___ files and data files for the software are placed in the folder you specify. Windows software typically contains a ___ program that guides you through the installation process.
A ___ is a form of legal protection that grants the author of an original “work” the right to copy, distribute, sell, and modify that work, except under special circumstances described by laws. A software ___ is a legal contract that defines the ways in which you may use a computer program.
Speaking. Discuss the following questions.
1. Where can I get software?
2. What is included in a typical software package?
3. How do I know if a software program will work on my computer?
4. Why is it necessary to install most software?
5. What is a software update?
6. How do I get rid of software?
7. Are all software licenses similar?
Critical thinking. Read the article and express you opinion on the problem.
Software Piracy
Software is easy to steal. You don’t have to walk out of a store with a $495 DVD Workshop software box under your shirt. You can simply borrow your friend’s DVD Workshop distribution CDs and install a copy of the program on your computer’s hard disk. It seems so simple that it couldn’t be illegal. But it is.
Piracy takes many forms. End-user piracy includes friends loaning distribution disks to each other and installing software on more computers than the license allows. Although it is perfectly legal to lend a physical object, such as a sweater, to a friend, it is not legal to lend digital copies of software and music because, unlike a sweater that can be worn by only one person at a time, copies of digital things can be simultaneously used by many people.
Counterfeiting is the large-scale illegal duplication of software distribution media, and sometimes even its packaging. According to Microsoft, many software counterfeiting groups are linked to organized crime and money-laundering schemes that fund a diverse collection of illegal activities, such as smuggling, gambling, extortion. Counterfeiting software is sold in retail stores and through online auctions– often the packaging looks so authentic that buyers have no idea they have purchased illegal goods.
Internet piracy uses the Web as a way to illegally distribute unauthorized software. The Business Software Alliance (BSA) estimates that more than 800.000 Web sites illegally sell or distribute software.
In many countries software pirates are subject to civil lawsuits for monetary damages and criminal prosecution, which can result in jail time and stiff fines. Is software piracy really damaging? Who cares if you use a program without paying for it? Software piracy is damaging because it has a negative effect on the economy. Software production fuels economic development of many countries. A BSA economic impact study concluded that lowering global piracy from an average of 36 % to only 26 % would add more than 1 million jobs and $400 billion in worldwide economic growth.
Decreases in software revenues can have a direct effect on consumers, too. When software publishers are forced to cut corners, they tend to reduce customer service and technical support. As a result, you, the consumer, get put on hold when you call for technical support, find fewer free support sites, and encounter customer support personnel who are only moderately knowledgeable about their products. The bottom line – software piracy negatively affects customer service. As an alternative to cutting support costs, some software publishers might build the cost of software piracy into the price of the software.
Some analysts suggest that people need more education about software copyrights and the economic implications of piracy. Other analysts believe that copyright enforcement must be increased by implementing more vigorous efforts to identify and prosecute pirates.
What do you think?
1. Do you believe that software piracy is a serious issue?
2. Do you know of any instances of software piracy?
3. Do you think that most software pirates understand that they are doing something illegal?
4. Should software publishers try to adjust software pricing for local markets?
Final test. Do the tasks in the following test.
1. All publicly available software programs adhere to the same licensing agreements. (True/False)
2. A(n) ___ operating system provides process and memory management services that allow two or more programs to run simultaneously.
3. Which of the following type of software is copyrighted software marked under a “try before buy” policy.
a) freeware b) shareware c) commercial software d) public domain software
4. ___ software helps you store, organize, update, and report information.
5. The microprocessor controls the operating system in your computer. (True/False)
6. A computer’s microprocessor understands both high-level and machine language. (True/False)
7. The operating system in many handheld computers is small enough to be stored in ROM. (True/False)
8. The software installation process includes which of the following activities:
a) analyzing the computer’s resources b) analyzing the computer’s hardware
c) updating necessary system files d) all of the above
9. MP3 encoding software is used to pull tracks off a CD and store it in a raw digital format on a computer’s hard disk. (True/False)
10. A(n) ___ translates all of the instructions in a program as a single batch, producing machine language instructions that are placed in a new file.
11. To start a software program, you run the program’s main ___ file.
12. Which of the following converts one computer instruction at a time into a machine language while the program is running?
a) a compiler b) an interpreter c) a translator d) none of the above
13. ___ language is the instruction set that is ‘hard wired’ within a microprocessor’s circuits.
14. A (n) ___ is a set of letters that shares a unified design.
15. Programmers first write instructions in a machine language and then translate them into a high-level language. (True/False)
16. System requirements specify both the operating system and the minimum hardware capacity necessary for a software product to work correctly. (True/False)
17. The ___ routine deletes a software program’s files and removes references to the program from the desktop and operating system files.
18. Which of the following is responsible for allocating specific areas of memory for each program running on your computer.
a) the microprocessor b) the operating system
c) RAM d) none of the above
19. Software counterfeiting and piracy does not include software that is distributed on the Internet. (True/False)
20. An auxiliary set of instructions that is used in conjunction with the main software program is called a(n) ___.
a) data file b) main executable file c) support program d) auxiliary file
Projects. Choose and perform one of the projects given.
1. Computer games are big business. They are exported worldwide and accessed by communities of online players around the globe. For this project gather information about the most internationally popular computer games. Try some of them yourself to see what they are all about. What effect, if any, would you expect these games to have on individual players living in the cultures of 1) industrialized countries, 2) Middle-eastern countries, and 3) developing countries? Summarize your ideas.
2. Use the Web and other resources to compile a list of the software used in your current or future career field. Are there standard packages that job applicants need to know how to use? If so, what can you find out about those packages on the Web. Also, make a list of the software packages you are familiar with. Use the software classification system. As you consider your career goals for the next year, list at least five additional software packages you would like to learn. Explain why they would be helpful.
Unit 4. FILE MANAGEMENT, VIRUS PROTECTION
AND BACKUP
TEXT A
Pre-reading. Match the meaning of the following English words with their Russian equivalents.
|
1. case sensitive |
a) папка |
|
2. root directory |
b) устройство (среда) хранения информации |
|
3. period |
c) превышать |
|
4. coding scheme |
d) символ подчеркивания, черта снизу |
|
5. storage medium |
e) звездочка (символ) |
|
6. exceed |
f) имя дисковода |
|
7. folder |
g) схема кодирования |
|
8. underscore |
h) корневой каталог |
|
9. drive letter |
i) точка |
|
10. asterisk |
j) чувствительный к регистру |
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
FILE BASICS
A computer file – or simply a “file” – is defined as a named collection of data that exists on a storage medium, such as a disk, CD, DVD, or tape. A file can contain a group of records, a document, a photo, music, a video, an e-mail message, or a computer program. Computer files have several characteristics, such as a name, format, location, size, and date.
Every file has a name and might also have a file extension. When you save a file, you must provide a valid file name that adheres to specific rules, referred to as file-naming conventions. Each operating system has a unique set of file-naming conventions. Figure 4 lists the file-naming conventions for the current versions of Windows.
|
Case sensitive |
No |
|
Maximum length of file name |
File name and extension cannot exceed 255 characters |
|
Spaces allowed |
Yes |
|
Numbers allowed |
Yes |
|
Characters not allowed |
* \ : < > | " / ? |
|
File names not allowed
|
Aux, Com1, Com2, Com3, Com4, Con, Lpt1, Lpt2, Lpt3, Prn, Nul
|
Fig. 4: Windows File-naming Conventions
DOS and Windows 3.1 limited file names to eight characters. With that limitation, it was often difficult to create descriptive file names As a result, files were sometimes difficult to locate and identify. Today, most operating systems allow you to use long file names.
Current versions of Windows support file names up to 255 characters long. That limitation includes the entire file path sometimes called a file specification—drive letter, folders, file name and extension.
C:\My Music\Reggae\Marley One Love.mp3
|
Drive letter |
Primary folder |
Secondary folder |
File name |
File extension |
An operating system maintains a list of files called a directory for each storage disk, tape, CD, or DVD. The main directory of a disk is referred to as the root directory. A root directory can be subdivided into smaller lists. Each list is called a subdirectory. When you use Windows, Mac OS, or a Linux graphical file manager, these subdirectories are depicted as folders. Folders can be created within other folders. (See the example, mentioned above) A folder name is separated from a drive letter and other folder names by a special symbol. In Microsoft Windows, this symbol is the backslash (\). By storing a file in a folder, you assign it a place in an organized hierarchy of folders and files.
If an operating system attaches special significance to a symbol, you might not be able to use it in a file name. For example, Windows uses the colon (:) character to separate the device letter from a file name or folder, as in C:Music. When you use Windows applications, avoid using the symbols: * \ < > | " / and ? in file names.
Some operating systems also contain a list of reserved words that are used as commands or special identifiers. You cannot use these words alone as a file name. Windows users should avoid using the following reserved words as file names: Nul, Aux, Com1, Com2, Com3, Com4, Con, Lpt1, Lpt2, Lpt3, and Prn.
Some operating systems are case sensitive, but not those you typically work with on personal computers. Feel free to use uppercase and lowercase letters in file names that you create on PCs and Macs.
You can also use spaces in file names. That’s a different rule than for e-mail addresses where spaces are not allowed. You’ve probably noticed that people often use underscores or periods instead of spaces in e-mail addresses such as Madi_Jones@msu.edu. That convention is not necessary in file names, so a file name such as Letter to Madi Jones is valid.
A file extension is an optional file identifier that is separated from the main file name by a period, as in Paint.exe. With some operating systems, such as Windows, file extensions work like tickets that admit people to different plays, movies, or concerts. If a file has the right extension for a particular application program, you'll see it in the list of files you can open with that software. A file extension is related to the file format, which is defined as the arrangement of data in a file and the coding scheme used to represent the data. Files containing graphics are usually stored using a different file format than files containing text. Most software have a native file format (.doc for MSWord, .pdf for AdobeAcrobat etc.)
To designate a file’s location, you must first specify where the file is stored. Each of PC’s storage devices is identified by a device letter (A:, C:, D:) – a convention that is specific to DOS and Windows. A device letter is usually followed by a colon, so drive A could be designated as A: or as 3.5" Floppy (A:).
The main hard disk drive is usually referred to as “drive C.” Additional storage devices can be assigned letters D through Z. Although most PCs stick to the standard of drive A for the floppy disk drive and drive C for the hard disk drive, the device letters for CD, Zip, and DVD drives are not standardized.
A file contains data, stored as a group of bits. The more bits, the larger the file. File size is usually measured in bytes, kilobytes, or megabytes. Compared to small files, large files fill up storage space more quickly, require longer transmission times, and are more likely to be stripped off e-mail attachments by a mail server.
Your computer keeps track of the date that a file was created or last modified. The file date is useful if you have created several versions of a file and want to make sure you know which version is the most recent.
Comprehension сheck. Mark the following statements as True or False.
1. When you create a file, you should give it a proper name according to file-naming conventions.
2. Windows limits the length of file names up to 265 characters.
3. Users must store a file in a folder to appoint it a place in a hierarchical structure of folders and files.
4. Operating systems add special significance to certain symbols that you should avoid in file names.
5. A file extension is a compulsory file identifier separated from the file name by a period.
6. The device letters for the floppy and hard disks are standardized.
Vocabulary practice
1. Match up the words that are similar in meaning.
|
1. stick; 2. particular; 3. contain; 4. conventions; 5. add importance; 6. be referred to as; 7. retrieve; 8. whole; 9. character; 10. assign; 11. proper; 12. arrangement; 13. alter. |
a) attach significance; b) symbol; c) layout; d)appoint; e) be defined as; f) modify; g) valid; h) adhere; i) rules; j) certain; k) include; l) strip off; m) entire. |
2. Fill in the blanks choosing out of the variants given.
1. A valid file requires adhering to specific rules called file-naming … .
a) conditions b) conventions c) conversions d) contents
2. Drive letter, folders, file name and extension restrict the whole file path which is referred to as a file … .
a) location b) identification c) specification d) format
3. A list of files for each storage medium is defined as a … .
a) scheme b) directory c) modification d) application
4. … e-mail addresses, a valid file name may contain spaces.
a) instead of b) compared to c) like d) unlike
5. A native file format is supported by most …, e. g. .doc for MSWord.
a) processors b) hardware c) software d) servers
6. A character generally following a device letter is a … .
a) backslash b) period c) asterisk d) colon
7. If a user wants to find the most recent version of a created file, the file … will be useful.
a) name b) size c) date d) extension
8. The file format means the … of data and a coding scheme representing the data.
a) management b) attachment c) appointment d) arrangement
9. To pad storage space, files of a bigger size require … time than small file
a) more b) less c) higher d) lower
3. Make two -word combinations using the words in columns and then fill in the gaps in the following sentences.
A: root B: words
maximum sensitive
application attachments
file directory
e-mail formats
reserved program
case length
1. Some operating systems which allow you to use uppercase and lowercase letters in file names are not … .
2. Large files can be easily stripped off … by mail server.
3. Graphical files and files containing text are saved in different … .
4. A … of file names is restricted in file-naming conventions.
5. The … is the main directory of a disk.
6. A file with the relevant extension for a particular … will be seen in the list of files of that software.
7. There are … that represent commands or special identifiers and can’t be used alone as a file name.
4. Fill in the gaps in the text.
A computer ___ is a named collection of data that exists on a storage medium, such as a hard disk, floppy disk, CD, DVD, or tape. Every file has a name and might also have a file extension. The rules that specify valid file names are called ___. These rules do not allow you to use certain characters or ___ words in a file name. A file ___ is usually related to a file format - the arrangement of data in a file and the coding scheme used to represent the data. A software program’s ___ file format is the default format for storing files created with that program.
A file’s location is defined by a file ___ sometimes called a “path”, which includes the storage device, folder(s), file name and extension. In Windows, storage devices are identified by a ___ letter, followed by a colon. An operating system maintains a list of files called a ___ for each storage disk, tape, CD, or DVD. The main directory of a disk is sometimes referred to as the ___ directory, which can be subdivided into several smaller lists called subdirectories that are depicted as ___.
Speaking. Discuss the following questions.
- What is a computer file?
- What are the rules for naming files?
- Is there a maximum length for file names?
- What is the purpose of folders?
- Why are certain characters not allowed in a file name?
- What are reserved words?
- What is the difference between e-mail addresses and file names?
- Are file extensions important?
- How can you designate a file’s location?
- What is the significance of a file’s size?
- Why is the file date useful?
Text B
Pre-reading. Match the English words with their Russian equivalents.
|
1. storage bin |
a) строка меню |
|
2. dialog box |
b) индексный файл |
|
3. tip |
c) диалоговое окно |
|
4. menu bar |
d) совет |
|
5. index file |
e) запоминающий буфер |
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
FILE MANAGEMENT
File management encompasses any procedure that helps you organize your computer-based files so that you can find and use them more efficiently. Depending on your computer’s operating system, you can organize and manipulate your files from within an application program or by using a special file management utility the operating system provides.
Application-based file management
Applications, such as word processing software or graphics software, typically provide a way to open files and save them in a specific folder on a designated storage device. Take a look at an example of the file management capabilities in a typical Windows application — Microsoft Word.
As you type the document, it is held in RAM. If you want to save the document, you click File on the menu bar, and then select the Save As option. The Save As dialog box opens and allows you to specify a name for the file and its location on one of your computer’s storage devices.
The difference between the two options is subtle, but useful. The Save As option allows you to select a name and storage device for a file, whereas the Save option simply saves the latest version of a file under its current name and at its current location. If you want to save a new file without a name, your application displays the Save As dialog box, even though you selected the Save option.
Windows explorer
As an example of a file management utility, take a closer look at Windows Explorer, a utility program bundled with the Windows operating system and designed to help you organize and manipulate the files stored on your computer.
The Windows Explorer window is divided into two “window panes” (see figure 5 on the following page).
In addition to locating files and folders, Windows Explorer provides a set of procedures that help you manipulate files and folders in the following ways:
- Rename
- Copy.
- Move. When you move a file, it is erased from its original location, so make sure you remember the new location of the file.
- Delete.
File management tips
The following tips pertain to managing files on your computer.
-Use descriptive names. Give your files and folders descriptive names, and avoid using cryptic abbreviations.
-Maintain file extensions. When renaming a file, keep the original file extension so that you can easily open it with the correct application software.
- Group similar files. Separate files into folders based on subject matter.
- Organize your folders from the top down. When devising a hierarchy of folders, consider how you want to access files and back them up.
- Do not mix data files and program files. Do not store data files in the folders that hold your software.
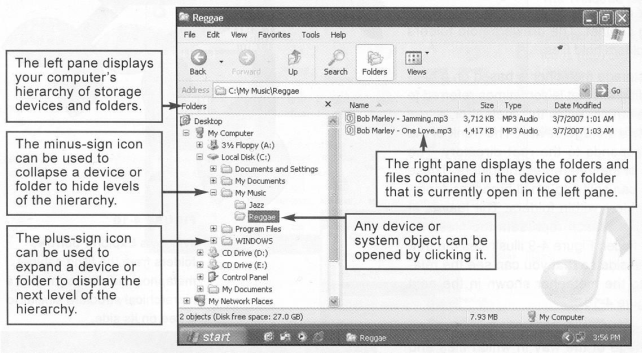
Fig. 5: The Windows Explorer window
- Don’t store files in the root directory. Although it is acceptable to create folders in the root directory, it is not a good practice to store programs or data files in the root directory of your computer’s hard disk.
- Access files from the hard disk. For best performance, copy files from floppy disks or CDs to your computer's hard disk before accessing them.
- Delete or archive files you no longer need. Deleting unneeded files and folders helps keep your list of files from growing to an unmanageable size.
- Be aware of storage locations. When you save files, make sure the drive letter and folder name specify the correct storage location.
- Back up! Back up your folders regularly.
Physical file storage
Before a computer can store a file on a disk, CD, or DVD, the storage medium must be formatted. The formatting process creates the equivalent of electronic storage bins by dividing a disk into tracks and then further dividing each track into sectors. Tracks and sectors are numbered to provide addresses for each data storage bin. The numbering scheme depends on the storage device and the operating system. On floppy, Zip, and hard disks, tracks are arranged as concentric circles; on CDs and DVDs, one or more tracks spiral out from the center of the disk.
To speed up the process of storing and retrieving data, a disk drive usually works with a group of sectors called a cluster or a “block”. The number of sectors that form a cluster varies, depending on the capacity of the disk and the way the operating system works with files. A file system's primary task is to maintain a list of clusters and keep track of which are empty and which hold data. This information is stored in a special index file. If your computer uses the FAT32 file system, for example, this index file is called the File Allocation Table (FAT). If your computer uses NTFS, it is called the Master File Table (MFT).
When you save a file, your PC’s operating system looks at the index file to see which clusters are empty. It selects one of these empty clusters, records the file data there, and then revises the index file to include the new file name and its location.
Comprehension check. Indicate the paragraph where the following ideas are found in the text .
1. It is preferable to maintain file extensions and not to store files in the root directory.
2. There is a slight difference between the Save option and the Save As option.
3. A special index file is required to keep track of a file’s location.
4. This program is related to the Windows operating system and exemplifies a file management utility.
5. The way to open and save a file on a specified storage medium depends on software applications.
6. Apart from locating files, it enables users to rename, copy, move and delete them.
Vocabulary practice
1. Match up the words that are opposite in meaning.
save distinct
empty display
additional include
subtle erase
hide basic
retrieve full
2. Fill in the blanks choosing out of the variants given.
1. To make storing and finding data fast, a disk drive deals with a … which is a group of sectors.
a) track b) bin c) cluster d) junction
2. You had better … cryptic abbreviations in files and folders.
a) give b) avoid c) access d) accept
3. You can avoid growing your list of files to an unmanageable size by … unnecessary files and folders.
a) saving b) deleting c) renaming d) moving
4. File … facilitates the process of organizing and manipulating your computer-based files.
a) location b) extension c) performance d) management
5. The operating system revises the index file to … the new file name and its location.
a) erase b) include c) number d) exclude
6. … a file is stored on a disk, CD, etc., the storage medium should be formatted.
a) before b) after c) while d) since
7. The pattern of … tracks and sectors is dependent on the storage medium and your PC’s operating system.
a) dividing b) selecting c) numbering d) arranging
3. Make three-word combinations using the words in columns and then fill in the gaps in the following sentences.
A: file B: sign C: option
save storage utility
master management table
data file bin
plus as icon
1. If you want to select a name and a storage device for a file, the … should be used.
2. … are designated addresses by numbering tracks and sectors.
3. A special … provided by the operating system helps you manage your files efficiently.
4. The … is used to display the next level of your computer’s hierarchy of storage devices and folders.
5. The … is the index file supported by the NFTS file system.
4. Fill in the gaps in the text.
File ___ provides any procedure that can help you organize your computer-based files so that you can find and use them more ___. File management uses tools provided with a software program to open and save files. Additional tools might enable you to ___ new files and folders, rename files, and delete them. The Save and Save As ___ boxes are examples of these file management tools.
Before a computer stores data on a disk, CD, or DVD, it creates the equivalent of electronic storage ___ by dividing the disk into ___, and then further dividing the disk into ___. This dividing process is referred to as ___. Each sector of a disk is numbered, providing a storage address that the operating system can track. Many computers work with a group of sectors, called a ___, to increase the efficiency of file storage operations.
Speaking. Discuss the following questions.
1. What does file management mean?
2. How does a software application help users manage files?
3. What is the difference between the Save option and the Save As option?
4. What is the example of a file management utility?
5. What is Windows Explorer designed for?
6 What can be done with the files and folders that are listed in Windows Explorer?
7. What file management tips should be followed while manipulating files?
8. What does the formatting process involve?
9. What is a cluster?
10. Is a file system’s primary or secondary task to keep track of which clusters keep data and which clusters don’t?
11. How does the operating system use an index file to help you save a file?
Text C
Pre-reading. Match the meaning of the following English words with their Russian equivalents.
|
computer virus |
вирусная подпись |
|
malicious code |
бот |
|
boot sector virus |
компьютерный вирус |
|
macro virus |
«Троянский конь» |
|
trigger event |
переключающее (триггерное) событие |
|
Trojan horse |
контрольная сумма |
|
keylogger |
клавиатурный шпион |
|
bot |
макровирус |
|
antivirus software |
вирус сектора загрузки |
|
checksum |
вредоносный код |
|
virus signature |
антивирусное программное обеспечение |
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
COMPUTER VIRUSES
Viruses are one of the biggest threats to the security of your computer files. In 1981, there was one known computer virus. Today, the count exceeds 100,000. Between 900 and 1,300 new viruses appear every month.
A computer virus is a set of program instructions that attaches itself to a file, reproduces itself, and spreads to other files. The term “computer virus” is often used to refer to any malicious code or software that invades a computer system. The term malicious code (sometimes called “malware”) refers to a program or set of program instructions designed to surreptitiously enter a computer and disrupt its normal work. Many types of malicious code, including viruses, worms, and Trojan horses, are created and unleashed by individuals referred to as “hackers” or “crackers”.
Viruses spread when people distribute infected files by exchanging disks and CDs, sending e-mail attachments, exchanging music on file-sharing networks, and downloading software from the Web. Many computer viruses infect files executed by your computer – files with extensions such as .exe, .com. or .vbs. When your computer executes an infected program, it also executes the attached virus instructions.
A virus can be classified as a file virus, boot sector virus, or macro virus. A file virus infects application programs, such as games. A boot sector virus infects the system files your computer uses every time you turn it on. These viruses can cause widespread damage to your computer files and recurring problems. A macro virus infects a set of instructions called a “macro” – a miniature program that usually contains legitimate instructions to automate document and worksheet production. When you view a document containing an infected macro, the macro virus duplicates itself into the general macro pool, where it is picked up by other documents. In addition to replicating itself, a virus might deliver a payload, which could be as harmless as displaying an annoying message or as devastating as corrupting the data on your computer’s hard disk. A trigger event, such as a specific date, can unleash some viruses. For example, the Michelangelo virus triggers on March 6, the birthday of artist Michelangelo.
A Trojan horse (sometimes simply called a “Trojan”) is a computer program that seems to perform one function while actually doing something else. Trojan horses are notorious for stealing passwords using a keylogger – a type of program that records your key-stroke.
Any software that can automate a task or autonomously execute a task when commanded to do so is called an intelligent agent. Because an intelligent agent behaves somewhat like a robot, it is often called a bot. Like a spider in its web, the person who controls many bot-infested computers can link them together into a network called a botnet. Botnets as large as 400,000 computers have been discovered by security experts.
Malicious Code Trends
|
Date |
Threats |
Trends |
|
1981 |
Cloner |
The first known virus begins to spread. Cloner infects files on disks formatted for Apple II computers. The prevalence of disk-borne viruses continues well into the1990s with Jerusalem (1987), Michelangelo (1992), and others.
|
|
1988 |
Internet Worm |
The first major worm attack over the Internet sets the stage for today's prolific crop of mass-mailing worms.
|
|
1998 |
Back Orifice |
First Trojan horse designed to allow a remote hacker to gain unauthorized access to a computer.
|
|
1999 |
Melissa |
Macro viruses, such as Melissa and l.aroux, are prevalent for several years and cause trouble by infecting Microsoft Word and Excel files.
|
|
2000 |
Love Letter |
One of the fastest spreading mass-mailing worms. Followed by Sobig, Blaster, and MyDoom (2004).
|
|
2001 |
Code Red |
Worms designed for Denial of Service attacks gather steam. Code Red, which targeted the White House, is followed by Blaster (2001) and Slammer (2003).
|
|
2002 |
Klez |
Klez is a mass-mailing worm that is particularly difficult to eradicate. Because the “From” address is spoofed, it is almost impossible to locate infected computers.
|
|
20Most notebook computers are equipped with several USB ports. 03 |
Mimail |
Social engineering takes center stage and users are confused by fake e-mails from seemingly legitimate companies, such as PayPal, Microsoft, and Wells Fargo.
|
|
2004 |
Sasser Netsky Xombe MyDoom, Zafi Bagle |
Worms, such as Sasser, begin to emerge that infect computers without user interaction, such as opening an infected e-mail attachment. Mass-mailing worms are still most prevalent. Worms that spread over instant messaging and handheld devices begin to emerge.
|
|
2005 |
Mytob Zotob Rbot |
Bots become one of the biggest security problems. Arriving as e-mail attachments, links embedded in e-mail messages, or from infected banner ads, bots install themselves on unprotected computers, which can then be controlled by unauthorized hackers and commandeered into botnets that launch spam and Denial of Service attacks.
|
These are the top three steps you can take to prevent your computer from becoming infected:
- Use antivirus software on every computing device you own.
- Keep software patches and operating system service packs up to date.
- Do not open suspicious e-mail attachments.
Antivirus software is a type of utility software that can look for and eradicate viruses, Trojan horses, bots, and worms. This essential software is available for handheld computers, personal computers, and servers. Popular antivirus software for personal computers includes McAfee VirusScan, Norton AntiVirus, and F-Secure Anti-Virus.
Antivirus software uses several techniques to find viruses. As you know, some viruses attach themselves to an existing program. The presence of such a virus often increases the length of the original program. The earliest antivirus software simply examined the programs on a computer and recorded their length. A change in the length of a program from one computing session to the next indicated the possible presence of a virus.
To counter early antivirus software, hackers became more cunning. They created viruses that insert themselves into unused portions of a program file without changing its length. Antivirus software developers fought back. They designed software that examines the bytes in an uninfected application program and calculates a checksum. A checksum is a number calculated by combining the binary values of all bytes in a file. Each time you run an application program, antivirus software calculates the checksum and compares it with the previous checksum. If any byte in the application program has changed, the checksum will be different, and the antivirus software assumes that a virus is present.
Today’s viruses, Trojan horses, bots, and worms are not limited to infecting program files, so modern antivirus software attempts to locate them by searching your computer’s files and memory for virus signatures. A virus signature is a section of program code, such as a unique series of instructions, that can be used to identify a known malicious program, much as a fingerprint is used to identify an individual.
Comprehension check. Choose the ending for each sentence from the two versions given.
|
1. Worm named Code Red was targeted |
a) White House; b) Bank of Scotland.
|
|
2. Any program designed to enter a computer and disrupt its normal operations is called
|
a) malicious code; b) utility.
|
|
3. Many types of malicious codes are created by |
a) the computer itself; b) individuals referred to as “hackers”.
|
|
4. A boot sector virus infects the system files your computer uses
|
a) every time you turn it on; b) when you are connected to the Internet.
|
|
5. A change in the length of a program from one computing session to the next |
a) indicated the possible presence of a virus; b) is a result of operation system work.
|
|
6. A checksum is |
a) a number calculated by combining the binary values of all bytes in a file; b) the cost of an antivirus program.
|
Vocabulary practice
1. Which word does not belong to the group?
a) virus, worm, Trojan horse, bot, file, botnet;
b) distribute, download, automate, infect, view, execute;
c) duplicates, instructions, infects, invades, behaves, spreads;
d) spider, programmer, hacker, user, server, developer;
e) individual, general, normal, personal, analytical, digital.
2. Fill in the blanks choosing from the variants given.
1. Does the term computer virus refer to any malicious code that … (makes up/invades) a computer system?
2. When your computer executes an infected program it … (executes/deletes) the attached virus instructions.
3. A trigger event, such as a specific date, can … (kill/destroy/unleash) some viruses.
4. Love letter is one of the … (slowest/fastest) spreading mass-mailing worms of all time.
5. Hackers created viruses that insert themselves into … (used/unused) portions of a program file without changing its length.
3. Transform the given sentences using the word(s) in brackets without any change in meaning.
1. A computer virus is a set of programs that attaches itself to a file (connecting).
2. If a document contains an infected macro, the macro virus duplicates itself into the general macro pool, where it is picked up by other documents (doubles, selected).
3. A virus might deliver a payload which could be both harmless and devastating (do no harm, corrupt).
4. Software that can automate a task when commanded to do so is called an intelligent agent (is able, is instructed).
5. A trigger event, such as a specific date, can unleash some viruses (particular, release).
6. Trojan horses are notorious for stealing passwords using a keylogger – a type of program that records your key-strokes (known, a sort).
4. Fill in the gaps in the text.
A computer virus is a set of program instructions that attaches itself to a file, reproduces itself, and spreads to the other files. You might encounter several types of viruses. A virus that attaches itself to an application program, such as a game utility, is known as a ___ virus. A boot ___ virus infects the system files your computer uses every time you turn it on. A ___ virus infects a set of instructions that automates document and worksheet production.
A Trojan horse is a computer program that seems to perform one function while actually doing something else. Such programs are notorious for stealing ___, although some delete files and cause other problems.
___ software can help prevent viruses from invading your computer system and can root out viruses that that take up residence. This software typically scans for a virus ___ and is sometimes referred to as virus scanning software.
Speaking. Discuss the following questions.
1. What is a computer virus?
2. How do viruses spread?
3. Are there different kinds of viruses?
4. What is a Trojan horse? What is a bot?
5. What is a botnet?
6. How can you avoid viruses and worms?
7. What is antivirus software? How does it work?
Text D
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
DATA BACKUP
Backup and restore procedures
Have you ever mistakenly copied an old version of a document over a new version? Has your computer's hard disk drive gone on the fritz? Did a virus wipe out your files? Has lightning “fried” your computer system? These kinds of data disasters are not rare; they happen to everyone. You can’t always prevent them, so you need a backup plan that helps you recover data that's been wiped out by operator error, viruses, or hardware failures.
A backup is a copy of one or more files that has been made in case the original files become damaged. A backup is usually stored on a different storage medium from the original files. For example, you can back up files from your hard disk to a different hard disk, a writable CD or DVD: tape, floppy disk, or Web site.
A good backup plan allows you to restore your computing environment to its pre-disaster state with a minimum of fuss. Unfortunately, no single backup plan fits everyone’s computing style or budget. You must devise your own backup plan that’s tailored to your particular computing needs.
A full-system backup contains a copy of every program, data, and system file on a computer. The advantage of a full-system backup is that you can easily restore your computer to its pre-disaster state simply by copying the backup files to a new hard disk. A full-system backup takes a lot of time, however, and automating the process requires a large-capacity tape backup device or a second hard disk drive.
A workable alternative to a full system backup is a “selective” backup that contains only your most important data files. The disadvantage of this backup strategy is that because you backed up only data files, you must manually reinstall all your software before restoring your data files.
If your strategy is to back up your important data files, the procedure can be simplified if you’ve stored all these files in one folder or its subfolders.
In addition to data files you create, a few other types of data files might be important to you. Consider making backups of these-files:
- Internet connection information
- E-mail folders
- E-mail address book
- Favorite URLs
- Downloads
Windows users often hear a variety of rumors about backing up the Windows Registry. The Registry, as it is usually called, is an important group of files the Windows operating system uses to store configuration information about all the devices and software installed on a computer system.
As simple as it sounds, backing up the Registry can present a bit of a problem because the Registry is always open while your computer is on. Windows users whose backup plans encompass all files on the hard disk must make sure their backup software provides an option for including the Windows Registry.
Your backup schedule depends on how much data you can afford to lose. If you’re working on an important project, you might want to back up the project files several times a day. Under normal use, however, most people schedule a once-a-week backup. If you work with a To Do list, use it to remind yourself when it is time to make a backup.
Store your backups in a safe place. Don’t keep them at your computer desk because a fire or flood that damages your computer could also wipe out your backups. Storing your backups at a different location is the best idea, but at least store them in a room apart from your computer.
Backup devices
The backup device you select depends on the value of your data, your current equipment, and your budget. Most computer owners use what they have — a writable CD drive, Zip drive, or floppy disk drive.
The major disadvantage of backing up your data on CDs and DVDs is that the writing process is slow — slower than writing data to tape or a removable hard disk. Further, although it is feasible to back up your entire system on a series of CDs or DVDs, you would have to use special backup software, monitor the backup process, and switch disks occasionally. CDs and DVDs are more practical for backing up a select group of important data files.
Zip disks with 100 MB or 250 MB capacity are sufficient for backups of documents and most digital graphics files. Several 750 MB Zip disks might be enough for backing up all your data files and could be feasible for a full-system backup if you have not installed lots of application software.
A second hard disk drive is a good backup option — especially if it has equivalent capacity to your main hard disk. This capacity allows the backup process to proceed unattended because you won’t have to swap disks or CDs. Speed-wise, a hard disk is faster than tape, CD, or DVD drives. Unfortunately, like your computer’s main hard disk, a backup hard disk is susceptible to head crashes, making it one of the least reliable storage options.
Network and internet backup
If your computer is connected to a local area network, you might be able to use the network server as a backup device. Before entrusting your data to a server, check with the network administrator to make sure you are allowed to store a large amount of data on the server. Because you might not want strangers to access your data, you should store it in a password-protected, non-shared folder. You also should make sure the server will be backed up on a regular basis so that your backup data won’t be wiped out by a server crash.
Several Web sites offer fee-based backup storage space. When needed, you can simply download backup files from the Web site to your hard disk. These sites are practical for backups of your data files, but space limitations and download times make them impractical for a full-system backup. Experts suggest that you should not rely on a Web site as your only method of backup. If a site goes out of business or is the target of a Denial of Service attack, your backup data might not be accessible.
Backup software
To make a backup, you can use backup software — a set of utility programs designed to back up and restore files. Backup software usually includes options that make it easy to schedule periodic backups, define a set of files that you want to regularly back up, and automate the restoration process.
Backup software differs from most copy routines because it typically compresses all the files for a backup and places them in one large file. Under the direction of backup software, this file can spread across multiple tapes if necessary. The file is indexed so that individual files can be located, uncompressed, and restored.
Boot disks
A boot disk is a floppy disk or CD containing the operating system files needed to boot your computer without accessing the hard disk. A barebones boot disk simply loads the operating system kernel. It is needed, if your hard disk fails or a virus wipes out the boot sector files on your hard disk, you will not be able to use your normal boot procedure.
To create an MS-DOS boot disk, insert a blank floppy disk in drive A. Open My Computer or Windows Explorer, and then right-click the Drive A icon. Select Format and check the box labeled Create an MS-DOS startup disk.
Сomprehension check. Match the beginnings of the sentences in the first column with the endings in the second one.
|
1. A backup is a copy of one or more files |
a) to restore your computing environment to its pre-disaster state with a minimum of fuss. |
|
2. A good backup plan allows you |
b) and automating the process requires a large capacity tape backup device or a second hard disk drive. |
|
3. You must devise your own backup plan |
c) that is tailored to your particular computing needs. |
|
4. A full-system backup takes a lot of time |
d) that has been made in case the original files become damaged. |
|
5. Your backup schedule depends on how much data |
e) value of your data, your current equipment, and your budget. |
|
6 The backup device you select depends on the |
f) you can afford to lose. |
|
7. If your computer is connected to a local area network |
g) you might be able to use the network server as a backup device. |
Vocabulary practice
1. Put the appropriate unscrambled words into the sentences on the right.
|
covreer evitartalen lailtsner emagad mumide |
1. Because you backed up only data files you must manually ___ all your software before restoring your data files. 2. You need a backup plan that helps you ___ data that’s been wiped out by operator error, viruses or hardware ___. 3. Store your backups in a safe place or a fire or flood that ___ your computer could also wipe out your backup. 4. A workable ___ to a full system backup is a selective backup that contains only your most important data files. 5. A backup is usually stored on a different storage ___ from the original files. |
2. Fill in the blanks choosing from the variants given.
1. A backup is usually … (detected/stored) on a different storage medium from the original files.
2. A workable alternative to a full system backup is a … (selective/overall) backup that contains only your most important data files.
3. Storing your backups at a different locations is … (not a good/the best) idea.
4. The backup device you select depends on … (how much data you can afford to lose/the value of your data/your current equipment and your budget).
5. A full-system backup … (can be done in no time/takes a lot of time).
6. Under normal use most people schedule … (an everyday backup/once-a-week backup).
3. Match the beginnings and the endings of the instructions/steps given and put them into correct order.
|
1. Your backup schedule depends on |
a) that is tailored to your particular computing needs. |
|
2. No single backup plan fits |
b) most people schedule a once-a-week backup. |
|
3. You can’t always prevent data disasters |
c) how much data you can afford to use. |
|
4. You must devise your own backup plan |
d) everyone’s computing style or budget. |
|
5. Under normal use |
e) but at least store them in a room apart from your computer. |
|
6. The best idea is storing your backups at a different location |
f) so you need a backup plan that helps you recover data that’s been wiped out. |
4. Fill in the gaps in the text.
A backup is a copy of one or more files that has been made in case the original files become damaged. For safety, a backup is usually stored on a different storage medium from the original files. A good backup plan allows you to ___ your computing environment to its pre-disaster state with a minimum of fuss.
No single backup plan fits everyone’s computing style or budget. Your personal backup plan depends on the files you need to back up, the hardware you have available to make backups, and your backup software. In any case, it is a good idea to back up the Windows ___ and make sure your files are free of ___. Backups should be stored in a safe place, away from the computer.
Backups can be recorded on floppy disks, writable CDs and DVDs, networks, Web sites, a second hard disk, or tapes. Many computer owners depend on writable CDs for backups, and use My Computer or Windows ___ to simply select files and copy files to the backup. ___ drives and backup software are typically used in business situations when a full-system backup is desirable. Backup software differs from most copy routines because it ___ all the files for a backup into one large file.
In addition to file backups, you should have a ___ disk containing the operating system files and settings needed to start your computer without accessing the hard disk.
Speaking. Discuss the following questions.
1. Why do you need to make backups?
2. What are the major strategies and plans of backup? What does their choice depend on?
3. What are the advantages and disadvantages of different backup devices?
4. What can you say about network and internet backup?
5. What can you say about backup software?
6. What is a boot disk? How can it be created?
Critical thinking. Read the article and express you opinion on the problem.
Computer Crime
It doesn’t take any special digital expertise to mastermind some computer crimes. Setting fire to a computer doesn’t require the same finesse as writing a stealthy virus, but both can have the same disastrous effect on data. “Old-fashioned” crimes, such as arson, that take a high-tech twist because they involve a computer can be prosecuted under traditional laws.
Traditional laws do not, however, cover the range of possibilities for computer crimes. Suppose a person unlawfully enters a computer facility and steals backup tapes. That person might be prosecuted for breaking and entering. But would common breaking and entering laws apply to a person who uses an off-site terminal to “enter” a computer system without authorization? And what if a person copies a data file without authorization? Has that file really been “stolen” if the original remains on the computer?
Many countries have computer crime laws that specifically define computer data and software as personal property. These laws also define as crimes the unauthorized access, use, modification, or disabling of a computer system or data. But laws don’t necessarily stop criminals. If they did, we wouldn’t have to deal with malicious code and intrusions.
A 1995 high-profile case involved a computer hacker named Kevin Mitnick, who was accused of breaking into dozens of corporate, university, government, and personal computers. Although vilified in the media, Mitnick had the support of many hackers and other people who believed that the prosecution grossly exaggerated the extent of his crimes. Nonetheless, Mitnick was sentenced to 46 months in prison and ordered to pay restitution in the amount of $4,125 during his three-year period of supervised release. The prosecution was horrified by such a paltry sum – an amount that was much less than its request for $1,5 million in restitution.
Forbes reporter Adam L. Penenberg took issue with the 46-month sentence imposed by Judge Marianne Pfaelzer and wrote, “This in a country where the average prison term for manslaughter is three years. Mitnick’s crimes were curiously innocuous. He broke into corporate computers, but no evidence indicates that he destroyed data. Or sold anything he copied. Yes, he pilfered software — but in doing so left it behind. This world of bits is a strange one, in which you can take something and still leave it for its rightful owner. The theft laws designed for payroll sacks and motor vehicles just don’t apply to a hacker.”
The U.S. Patriot Act and the Cyber-Security Enhancement Act carry even stiffer penalties – anywhere from 10 years to life in prison.
A CNET reporter questions the harshness of such penalties: “What bothers me most is that here in the United States, rapists serve, on average, 10 years in prison. Yet if, instead of assaulting another human being, that same person had released a virus on the Net, the criminal would get the same or an even harsher sentence.”
Law makers hope that stiff penalties will deter cyber criminals. U. S. Attorney John McKay is quoted as saying, “Let there be no mistake about it, cyber-hacking is a crime. It harms persons, it harms individuals, it harms businesses.
These cases illustrate our culture's ambivalent attitude toward computer hackers. On the one hand, they are viewed as evil cyberterrorists who are set on destroying the glue that binds together the Information Age. From this perspective, hackers are criminals who must be hunted down, forced to make restitution for damages, and prevented from creating further havoc.
From another perspective, hackers are viewed more as Casper the Friendly Ghost in cur complex cybermachines – as moderately bothersome entities whose pranks are tolerated by the computer community, along with software bugs. Seen from this perspective, a hacker's pranks are part of the normal course of study that leads to the highest echelons of computer expertise.
What do you think?
- Should a computer virus distribution sentence carry the same penalty as
manslaughter?
- Should it be a crime to steal a copy of computer data while leaving the original data
in place and unaltered?
- Should hackers be sent to jail if they cannot pay restitution to companies and
individuals who lost money as the result of a prank?
- Do you think that a hacker would make a good consultant on computer security?
Final test. Do the tasks in the following test.
1. A (n) ___ is a copy of one or more files that has been made in case the original files become damaged.
2. The Windows ___ is an important group of files that the Windows operating system uses to store configuration information about all the devices and software installed on a computer system.
3. The main directory of a disk is referred to as the ___ directory.
4. The main hard disk drive on a PC is often referred to as “drive C”. (True/False)
5. A filename extension is usually related to a file ___, which is the arrangement of data in a file and the coding scheme used to represent the data.
6. Antivirus software is 100% reliable when it comes to protecting your computer from viruses. (True/False)
7. A file specification or path typically includes all of the following information EXCEPT ___.
a) the file author b) the file name c) the file extension d) the drive letter
8. ___ software is a set of utility programs that looks for and eradicates viruses, worms, and Trojan horses.
9. File-naming ___ are a set of rules for naming files.
10. The easiest way to convert a file from one format to another is to find an application program that works with both file formats. (True/False)
11. Deleting a file’s icon from a directory does not necessarily remove the data from the disk. (True/False)
12. A computer ___ is a set of program instructions that attaches itself to a file, reproduces itself, and spreads to other files.
13. A root directory typically contains smaller ___, often depicted as folders in graphical user interfaces.
14. A (n) ___ is a computer program that seems to perform one function while actually doing something else.
15. A virus can be spread if people distribute infected files by ___.
a) exchanging disks or CDs b) sending e-mail attachments
c) downloading software from the Web d) all of the above
16. You should update your antivirus software regularly. (True/False)
17. Bot-infected computers linked together into a network is called a(n) ___.
18. A virus ___ is a section of the virus program that can be used to identify a known virus.
19. Computer virus trigger events are often tied to a specific date. (True/False)
20. The file ___ helps you keep track of the most current version of your file when you have saved several versions.
Projects. Choose and perform one of the projects given.
1. Select one of the following statements and argue for or against it:
- People have the “right” to hone their computing skills by breaking into computers.
- A person who creates a virus is perfectly justified in releasing it if the purpose is to make everyone aware of these security breaches.
- Computer crimes are no different from other crimes, and computer criminals should be held responsible for the damage they cause.
![]()
![]() 2. Suppose you are a reporter for a local television station. Your assignment is to create a 90-second story about new emerged virus for your local TV news show. The basic objectives of the story are (1) to inform about the ways of spreading this virus and attributes that enable a person to find out presence of this particular virus and (2) to provide a set of concrete steps that a person could take to minimize the consequences for his computer and get rid of the virus. Of course, the network wants the story to be interesting, so you have to include a human-interest angle. Write the script for the story and include notes about the visuals that will appear.
2. Suppose you are a reporter for a local television station. Your assignment is to create a 90-second story about new emerged virus for your local TV news show. The basic objectives of the story are (1) to inform about the ways of spreading this virus and attributes that enable a person to find out presence of this particular virus and (2) to provide a set of concrete steps that a person could take to minimize the consequences for his computer and get rid of the virus. Of course, the network wants the story to be interesting, so you have to include a human-interest angle. Write the script for the story and include notes about the visuals that will appear.
1


про публікацію авторської розробки
Додати розробку
